不,你不会讨厌”yan85”的,因为后面的还有”yan85_64”。*_*
Reverse Engineering level1.0 这题很简单哇,就是把输入的字符串转成了ascii。对应输入即可获得flag
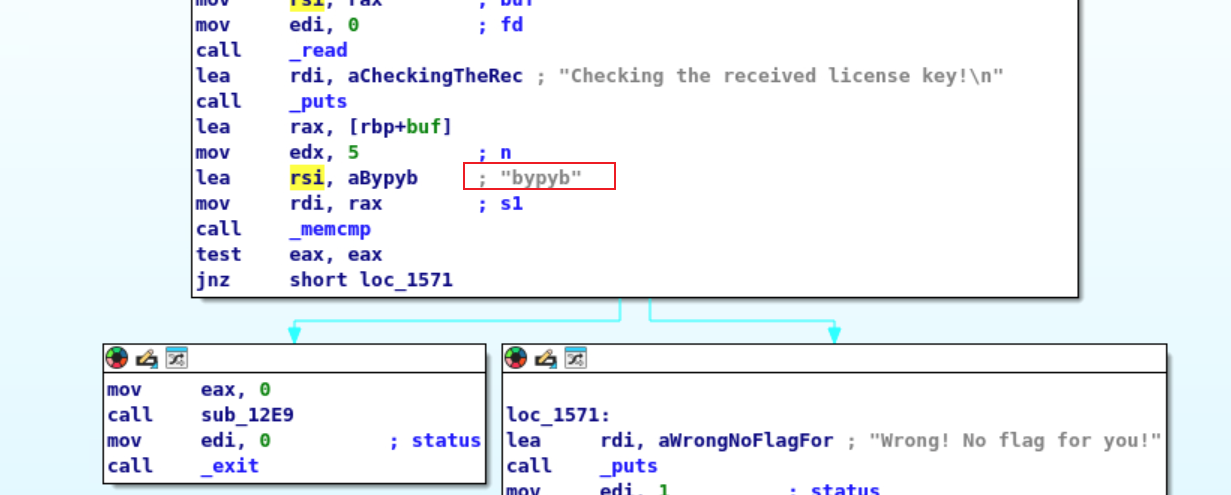
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 Ready to receive your license key!quit Initial input:71 75 69 74 0 a The mangling is done! The resulting bytes will be used for the final comparison.Final result of mangling input:71 75 69 74 0 a Expected result:63 6 c 6 a 79 62 Checking the received license key!
level1.1 这下没有回显了,只能通过工具逆向一下子了。
也很简单啊,直接看到了匹配的字符串。
level2.0 依然,使用IDA 看看:
但是输入会把最后两个字节翻转。最后输入xzujs即可。
level2.1 依然是,没有回显。简单查看一下逆向出来的源码。
1 2 3 4 5 6 7 8 movzx eax , byte ptr [rbp +buf+2 ]mov byte ptr [rbp +var_10], al movzx eax , byte ptr [rbp +buf+3 ]mov byte ptr [rbp +var_10+1 ], al movzx eax , byte ptr [rbp +var_10+1 ]mov byte ptr [rbp +buf+2 ], al movzx eax , byte ptr [rbp +var_10]mov byte ptr [rbp +buf+3 ], al
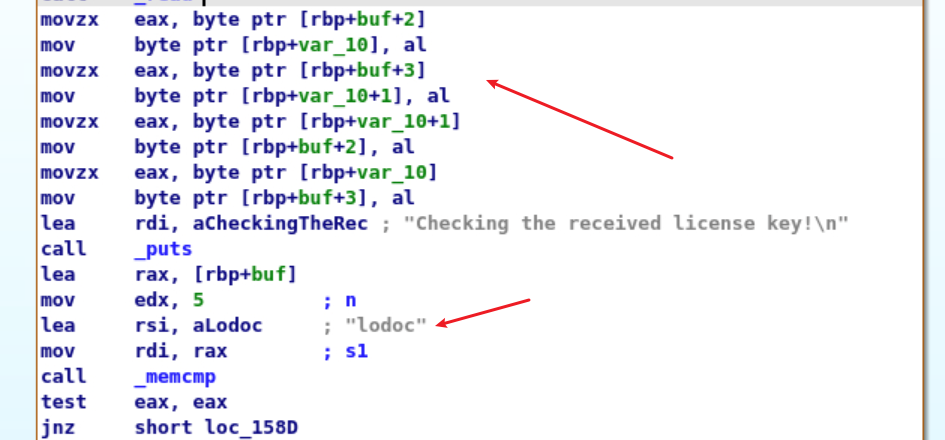
其中,rbp+buf是用户输入的地址。按照逻辑分析:该代码将用户输入的第3个字节给了rbp+var_10位置。第4个字节给了rbp+var_10+1位置,随后第4个字节给了第3个字节位置。第3个字节给了第4个字节位置。综合起来即,将用户输入的第三、四个字节位置交换。
那么输入loodc即可。
level3.0 1 2 3 4 5 6 7 8 9 10 quit Initial input:71 75 69 74 0 a This challenge is now mangling your input using the `reverse` mangler.This mangled your input, resulting in:0a 74 69 75 71
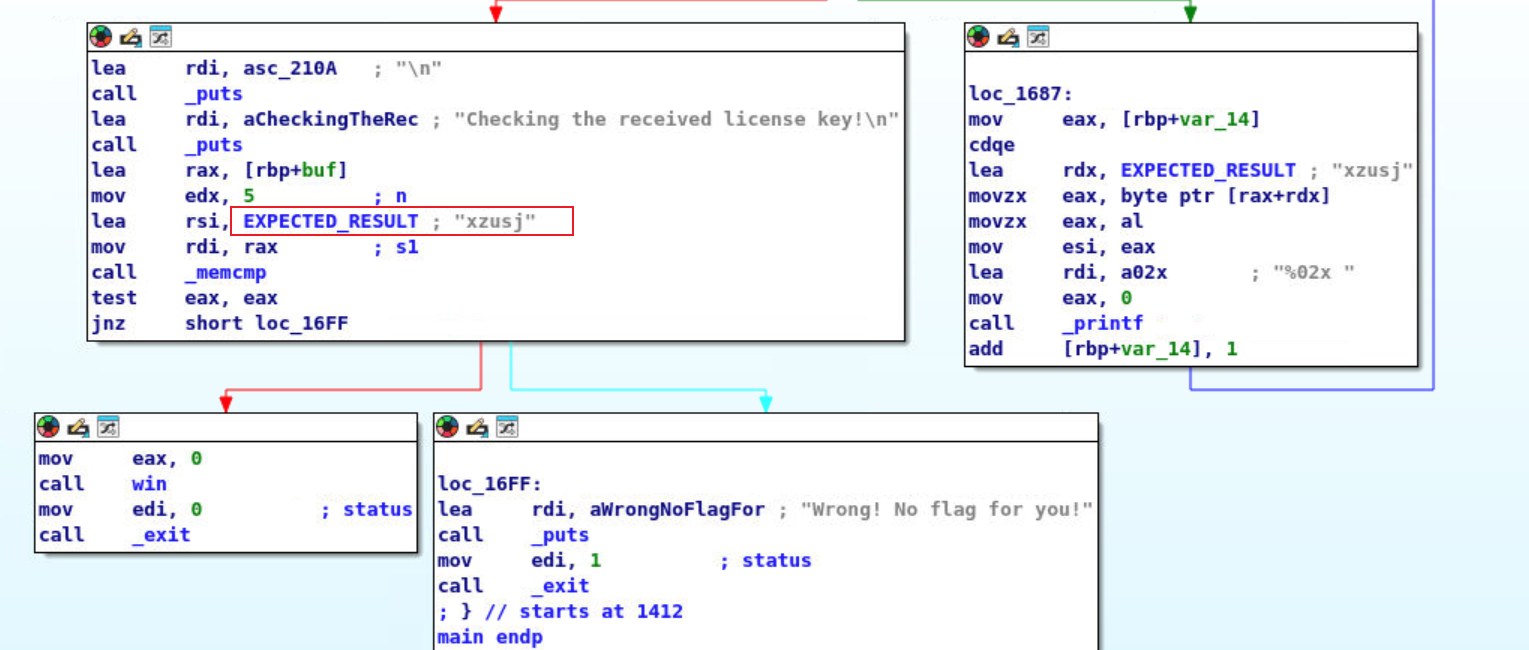
显然,这是将输入进行逆序了。
其实也不用IDA,通过回显的ASCII码可以推出要的结果。
最后输入sikky即可。
level3.1 查看源码:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 loc_153E: mov eax , [rbp +var_14]cdqe movzx eax , byte ptr [rbp +rax +buf]mov [rbp +var_16], al mov eax , 4 sub eax , [rbp +var_14]cdqe movzx eax , byte ptr [rbp +rax +buf]mov [rbp +var_15], al mov eax , [rbp +var_14]cdqe movzx edx , [rbp +var_15]mov byte ptr [rbp +rax +buf], dl mov eax , 4 sub eax , [rbp +var_14]cdqe movzx edx , [rbp +var_16]mov byte ptr [rbp +rax +buf], dl add [rbp +var_14], 1
cdqe指令:EAX符号位拓展到RAX
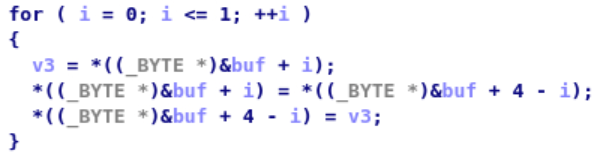
有点抽象的是,无法知道[rbp+var_14]的值,因此手动分析不出来哇。通过IDA查看源码,发现循环了两次,第一次是交换第一个字节和第5个字节。第二次是交换第二个字节和第4个字节。因此就是一个逆序。
然后,
最后输入ruhsi即可。
level4.0 1 2 3 4 5 6 7 8 9 10 quit Initial input:71 75 69 74 0 a This challenge is now mangling your input using the `sort` mangler.This mangled your input, resulting in:0a 69 71 74 75
最后一个字节,去了第一个位置。第三个字节去了第二个位置,第一个字节去了第三个位置,第四个位置没动,第二个字节去了第五个位置。
66 71 72 77 78,这是期待的字符串,也就是fqrwx
最后输入xrfwq即可。
qfxwr
level4.1 这道题也是一样的,按照上面的逻辑进行翻转。
1 2 3 4 5 6 7 8 9 10 11 12 for ( i = 0 ; i <= 3 ; ++i )for ( j = 0 ; j < 4 - i; ++j )if ( *((_BYTE *)&buf + j) > *((_BYTE *)&buf + j + 1 ) )1 );1 ) = v3;
分析一下,i = 0 的情况下,j由0到3,前五个字节。那么这里会有一个判断,即将ascii值最大的字节放至第5个位置;i = 1的情况下,j由0到2,前4个字节。将ascii值最大的字节放至第4个位置。以此类推。这是冒泡排序,对前5个字节进行冒泡排序。将ascii码值由小到大排序。
最后输入almrv的任意排序即可。因此,我在level4.0发现的规律是错误的。
level5.0 This challenge is now mangling your input using the xor mangler with key 0xb7
与0xb7异或。异或的操作是可逆的,那么再异或回去就好了。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 Type "help" , "copyright" , "credits" or "license" for more information.>>> 0xc3 ^ 0xb7 116 >>> hex (0xc3 ^ 0xb7 )'0x74' >>> hex (0xc2 ^ 0xb7 )'0x75' >>> hex (0xdf ^ 0xb7 )'0x68' >>> hex (0xc7 ^ 0xb7 )'0x70' >>> hex (0xc4 ^ 0xb7 )'0x73' >>>
用python终端,即可。最终输入tuhps即可。
level5.1 1 2 for ( i = 0 ; i <= 4 ; ++i )0x41u ;
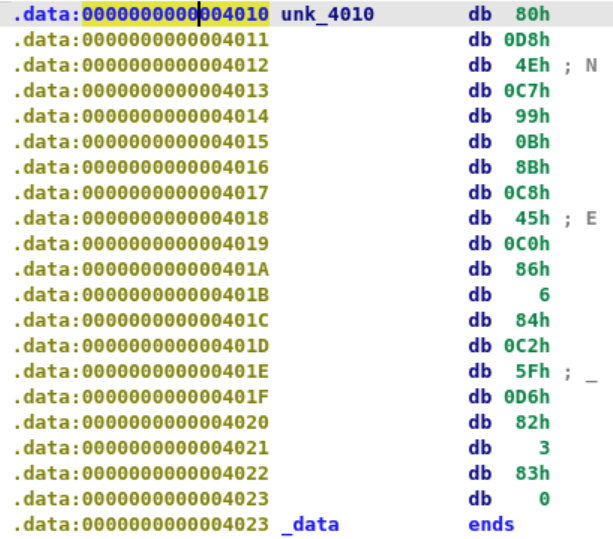
异或的字节为0x41,目标字符串是.data:0000000000004010 a056 db '0',27h,27h,'56',0
异或一下。最终输入qfftw即可。
level6.0 This challenge is now mangling your input using the xor mangler with key 0xbf46
This challenge is now mangling your input using the sort mangler.
This challenge is now mangling your input using the swap mangler for indexes 0 and 9.
强度一下就上来啦,xor,sort和swap三种方法。
目标
字符串为:cd 20 25 27 27 28 31 35 c8 20 ce cf d1 d5 d9 dc,写个脚本跑就好了。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 from pwn import *"/challenge/babyrev_level6.0" )0x20 ,0x20 ,0x25 ,0x27 ,0x27 ,0x28 ,0x31 ,0x35 ,0xc8 ,0xcd ,0xce ,0xcf ,0xd1 ,0xd5 ,0xd9 ,0xdc ]"" for i in range (0 ,len (hex_string) - 1 , 2 ):print (i)chr (hex_string[i] ^ 0xbf )chr (hex_string[i+1 ] ^ 0x46 )print (payload)'Ready to receive your license key!\n' ,payload)print (data.decode())
因为有sort的关系,并且最终的结果也确实sort后swap就能达到。因此只需要将目标字符串从小到大排序后,异或0xbf46即可。
level6.1
目标字符串为0x80, 0xD8, 0x4E, 0xC7, 0X99, 0x0B, 0x8B, 0xC8, 0x45, 0xC0, 0x86, 0x06, 0x84, 0xC2, 0x5F, 0xD6, 0x82, 0x03, 0x83
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 for ( i = 0 ; i <= 18 ; ++i )3 ;if ( i % 3 == 2 )0xEBu ;else if ( v3 <= 2 )if ( v3 )if ( v3 == 1 )0x37u ;else 0xF1u ;for ( j = 0 ; j <= 8 ; ++j )18 - j);18 - j) = v4;for ( k = 0 ; k <= 18 ; ++k )if ( k % 2 )if ( k % 2 == 1 )0x46u ;else 0x1Du ;
最终脚本为:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 from pwn import *"/challenge/babyrev_level6.1" )0x80 , 0xD8 , 0x4E , 0xC7 , 0X99 , 0x0B , 0x8B , 0xC8 , 0x45 , 0xC0 , 0x86 , 0x06 , 0x84 , 0xC2 , 0x5F , 0xD6 , 0x82 , 0x03 , 0x83 ]"" for i in range (19 ):if i % 2 == 1 :0x46 else :0x1d for i in range (9 ):18 - i]18 - i] = tempfor i in range (len (hex_string)):if i % 3 == 2 :0xeb elif i % 3 == 1 :0x37 else :0xf1 for i in range (len (hex_string)):chr (hex_string[i])print (payload)'Ready to receive your license key!\n' ,payload)print (data.decode())
逆序进行即可。还是比较简单的。
level7.0 1 2 3 4 5 6 7 8 This challenge is now mangling your input using the `sort` mangler.This challenge is now mangling your input using the `swap` mangler for indexes `16 ` and `21 `.This challenge is now mangling your input using the `swap` mangler for indexes `9 ` and `22 `.This challenge is now mangling your input using the `swap` mangler for indexes `3 ` and `6 `.This challenge is now mangling your input using the `reverse` mangler.Expected result:79 78 78 68 72 73 72 72 72 74 70 6 f 6 f 6 d 6 c 6 a 77 67 65 62 64 62 64 61 61 61
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 from pwn import *"/challenge/babyrev_level7.0" )0x79 , 0x78 , 0x78 , 0x68 , 0x72 , 0x73 , 0x72 , 0x72 , 0x72 , 0x74 , 0x70 , 0x6f , 0x6f , 0x6d , 0x6c , 0x6a , 0x77 , 0x67 , 0x65 ,0x62 , 0x64 , 0x62 , 0x64 , 0x61 , 0x61 , 0x61 ]"" for i in range (len (hex_string)):chr (hex_string[i])print (payload)'Ready to receive your license key!\n' ,payload)print (data.decode())
因为sort在第一个的关系,因此实际上我们需要的是找到expected result即可。
level7.1 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 for ( i = 0 ; i <= 13 ; ++i )28 - i);28 - i) = v6;for ( j = 0 ; j <= 27 ; ++j )for ( k = 0 ; k < 28 - j; ++k )if ( *((_BYTE *)&buf + k) > *((_BYTE *)&buf + k + 1 ) )1 );1 ) = v5;for ( m = 0 ; m <= 13 ; ++m )28 - m);28 - m) = v4;for ( n = 0 ; n <= 28 ; ++n )switch ( n % 5 )case 0 :0x75u ;break ;case 1 :0x7Eu ;break ;case 2 :1u ;break ;case 3 :0x3Du ;break ;case 4 :0xC5u ;break ;default :continue ;
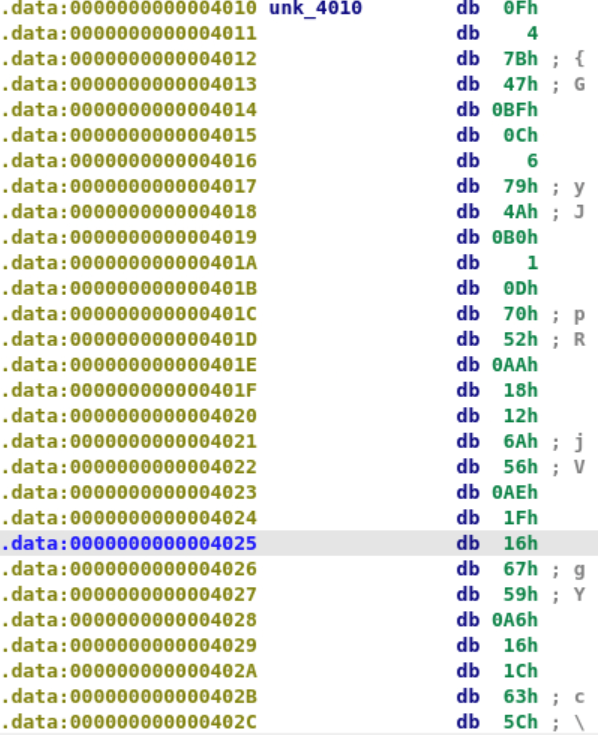
1 0x0f , 0 x04, 0 x7b, 0 x47, 0 xbf, 0 x0c, 0 x06, 0 x79, 0 x4a, 0 xb0, 0 x01, 0 x0d, 0 x70, 0 x52, 0 xaa, 0 x18, 0 x12, 0 x6a, 0 x56, 0 xae, 0 x1f, 0 x16, 0 x67, 0 x59, 0 xa6, 0 x16, 0 x1c, 0 x63, 0 x5c
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 from pwn import *"/challenge/babyrev_level7.1" )0x0f , 0x04 , 0x7b , 0x47 , 0xbf , 0x0c , 0x06 , 0x79 , 0x4a , 0xb0 , 0x01 , 0x0d , 0x70 , 0x52 , 0xaa , 0x18 , 0x12 , 0x6a , 0x56 , 0xae , 0x1f , 0x16 , 0x67 , 0x59 , 0xa6 , 0x16 , 0x1c , 0x63 , 0x5c ]"" for i in range (29 ):5 if d == 0 :0x75 elif d == 1 :0x7e elif d == 2 :0x01 elif d == 3 :0x3d else :0xc5 for i in range (len (hex_string)):chr (hex_string[i])print (payload)'Ready to receive your license key!\n' ,payload)print (data.decode())
level8.0 1 2 3 4 5 6 7 8 This challenge is now mangling your input using the `swap` mangler for indexes `5 ` and `22 `.This challenge is now mangling your input using the `reverse` mangler.This challenge is now mangling your input using the `xor` mangler with key `0 x3c7c`This challenge is now mangling your input using the `sort` mangler.This challenge is now mangling your input using the `swap` mangler for indexes `18 ` and `33 `.This challenge is now mangling your input using the `reverse` mangler.This challenge is now mangling your input using the `swap` mangler for indexes `3 ` and `10 `.5f 5 e 46 53 58 57 57 57 56 56 5 a 52 52 4 e 4 e 4 c 4 a 5 b 1 f 1 f 1 f 1 b 19 16 16 14 14 14 12 11 0 d 0 c 0 b 08 06 05
虽然有这么多层修改,但是只需要关心sort前的修改即可。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 from pwn import *"/challenge/babyrev_level8.0" )0x5f , 0x5e , 0x46 , 0x53 , 0x58 , 0x57 , 0x57 , 0x57 , 0x56 , 0x56 , 0x5a , 0x52 , 0x52 , 0x4e , 0x4e , 0x4c , 0x4a , 0x5b , 0x1f , 0x1f , 0x1f , 0x1b , 0x19 , 0x16 , 0x16 , 0x14 , 0x14 , 0x14 , 0x12 , 0x11 , 0x0d , 0x0c , 0x0b , 0x08 , 0x06 , 0x05 ]"" for i in range (len (hex_string)):if i % 2 == 0 :0x3c else :0x7c 1 ]5 ]5 ] = reversed_hex_string[22 ]22 ] = tempfor i in range (len (reversed_hex_string)):chr (reversed_hex_string[i])print (payload)'Ready to receive your license key!\n' ,payload)print (data.decode())
level8.1 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 for ( i = 0 ; i <= 17 ; ++i )36 - i);36 - i) = v7;for ( j = 0 ; j <= 36 ; ++j )if ( j % 2 )if ( j % 2 == 1 )0xA4u ;else 0x48u ;for ( k = 0 ; k <= 17 ; ++k )36 - k);36 - k) = v6;for ( m = 0 ; m <= 17 ; ++m )36 - m);36 - m) = v5;for ( n = 0 ; n <= 36 ; ++n )switch ( n % 5 )case 0 :0x5Cu ;break ;case 1 :0xA3u ;break ;case 2 :0xBDu ;break ;case 3 :0x29u ;break ;case 4 :0x6Cu ;break ;default :continue ;
1 0x79 , 0 x76, 0 x8c, 0 xe8, 0 x55, 0 x8e, 0 x93, 0 x75, 0 x0b, 0 xbc, 0 x64, 0 x69, 0 x9b, 0 xe8, 0 x5d, 0 x97, 0 x9d, 0 x77, 0 x10, 0 xb2, 0 x7b, 0 x6e, 0 x9b, 0 xe9, 0 x4b, 0 x93, 0 x87, 0 x6b, 0 x13, 0 xbd, 0 x75, 0 x60, 0 x9b, 0 xf9, 0 x53, 0 x8f, 0 x93
1 2 3 4 5 6 7 8 9 movzx eax , byte ptr [rbp +buf+3 ] # byte ptr [rbp + buf + 3 ]mov [rbp +var_4C], al movzx eax , byte ptr [rbp +var_28+4 ] # byte ptr [rbp + buf + 6 ] mov [rbp +var_4B], al movzx eax , [rbp +var_4B]mov byte ptr [rbp +buf+3 ], al movzx eax , [rbp +var_4C]mov byte ptr [rbp +var_28+4 ], al # 交换3 和6 mov [rbp +var_40], 0
1 2 3 4 5 6 7 8 movzx eax , byte ptr [rbp +var_20+6 ] # 等价为 byte ptr [rbp + buf + 16 ]mov [rbp +var_4E], al movzx eax , byte ptr [rbp +var_10] # 等价为 byte ptr [rbp + buf + 20 ]mov [rbp +var_4D], al movzx eax , [rbp +var_4D]mov byte ptr [rbp +var_20+6 ], al # 交换16 和20 movzx eax , [rbp +var_4E]mov byte ptr [rbp +var_10], al
动态调试:
1 2 3 4 5 6 7 8 原始输入:22 ---- 32 0x5ee6a471a571 (断点地址)0x5ee6a471a5de
1 2 3 4 xwwtngaurrlkodniozqnvoyennptjlevqxyqm 3 ---- 12 xwwtngaurrlkodniozqnvoqennptjlevyxyqm mqyxyveljtpnneqovnqzoindoklrruagntwwx mqynyveljtpnxeqovnqzoindoklrruagntwwx
调试过程中,发现两个swap的具体交换位置。然后写exp:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 from pwn import *"/challenge/babyrev_level8.1" )0x79 , 0x76 , 0x8c , 0xe8 , 0x55 , 0x8e , 0x93 , 0x75 , 0x0b , 0xbc , 0x64 , 0x69 , 0x9b , 0xe8 , 0x5d , 0x97 , 0x9d , 0x77 , 0x10 , 0xb2 , 0x7b , 0x6e , 0x9b , 0xe9 , 0x4b , 0x93 , 0x87 , 0x6b , 0x13 , 0xbd , 0x75 , 0x60 , 0x9b , 0xf9 , 0x53 , 0x8f , 0x93 ]"" print (len (hex_string))for i in range (37 ):if i % 5 == 0 :0x5c elif i % 5 == 1 :0xa3 elif i % 5 == 2 :0xbd elif i % 5 == 3 :0x29 else :0x6c for i in range (37 ):if i % 2 == 1 :0xa4 else :0x48 3 ]3 ] = hex_string[12 ]12 ] = tempfor i in range (18 ):36 - i]36 - i] = temp22 ]22 ] = hex_string[32 ]32 ] = tempfor i in range (len (hex_string)):chr (hex_string[i])print (payload)'Ready to receive your license key!\n' ,payload)print (data.decode())
level9.0 看源码:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 v12 = ((unsigned __int64)bin_padding & 0xFFFFFFFFFFFFF000L L) - 4096 ;do while ( !mprotect((void *)((v3 << 12 ) + v12), 0x1000u LL, 7 ) );for ( i = 0 ; i <= 4 ; ++i )printf ("Changing byte %d/5.\n" , (unsigned int )(i + 1 ));printf ("Offset (hex) to change: " );"%hx" , &v5);printf ("New value (hex): " );"%hhx" , &v4);printf ("The byte has been changed: *%p = %hhx.\n" , (const void *)(v12 + v5), v4);
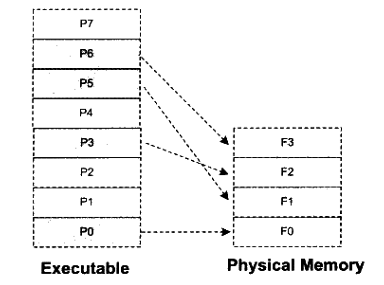
关于可执行文件的装载——页映射(理解上述源码的v12是什么)
静态装载 ——程序执行时所需要的指令和数据必须在内存中才能够正常运行,最简单的办法就是将程序运行所需要的指令和数据全都装入内存中,这样程序就可以顺利运行,这就是最简单的静态装入的办法。
**问题:**很多情况下程序所需要的内存数量大于物理内存的数量。
根本的解决办法是添加物理内存 。相对于磁盘来说,内存是昂贵的,因此人们想尽各种办法,希望能够不添加内存的情况下,让更多的程序运行起来,尽可能有效地利用内存。
那么为了良好地解决这个问题,研究人员发现,程序运行时是有局部性原理的,所以,将程序最常用的部分驻留在内存中,而将一些不太常用的数据存放在磁盘里面,这就是动态装载的基本原理。动态装载的思想是程序用到哪个模块,就将哪个模块装入内存,如果不用就暂时不装入,存放在磁盘中。
页映射 ——页映射不是一下子就把程序所有的数据和指令都装入内存,而是将内存和所有磁盘中的数据和指令按照“页(Page)”为单位划分成若干个页,以后所有的装载和操作的单位就是页。硬件规定的页的大小 由4096字节、8192字节、2MB、4MB等,最常见的Intel IA32处理器一般都是用4096字节。这题所使用到的分页也是4096字节为一页。
假设程序所有的指令和数据的总和为32KB,机器为32位有16KB的内存,每个页大小为4096字节。那么程序总共被分为8个页。可人为将它们编号P0~P7。很明显,16KB的内存无法同时将32KB的程序装入,那么将按照动态装入的原理来进行整个装入过程。如果程序刚开始执行时的入口地址在P0,这时装载管理器发现程序的P0不在内存中,于是将内存F0分配给P0,并且将P0的内容装入F0;运行一段时间以后,程序需要用到P5,于是装载管理器将P5装入F1;就这样,映射关系如下所示:
【来源:《程序员的自我修养》P156】
可以知道,v12计算得出上一页的起始地址。一页为4096字节。
解题思路:看到了if memcmp分支的条件。在ida中查看。其是jne,并且根据查表:Intel x86 JUMP quick reference ,可知jne的opcode是75,我们将其改成74即可控制分支。
根据思路,我们需要修改jne的opcode,通过gdb调试一下能够知道偏移量为0x27c1。最后我们只需要修改该位置的opcode为74,即可拿到flag。
level9.1 思路同上,偏移为0x1789,不过这题用gdb调试的时候,没有main这个符号。可以设置断点在_start处,然后一步步调试。到main处的时候,就能拿到main的地址。然后使用disassemble 起始地址,终止地址来查看这个地址区间的反汇编结果。然后就能查看jne指令的地址。最后算出偏移为0x1789,再修改opcode就行了。
level10.0 只能修改一个字节,但是够了。思路还是以上的思路。算出偏移地址为:0x1F17
level10.1 gdb的finish命令能够帮助快速执行完当前函数,断点可以打在memcmp函数这儿。偏移量为0x201e
level11.0 思路一致,只不过这时需要修改的是两个jne指令为jn指令,所以需要找到两个偏移量。还是按照前面题目的思路,找到的两个偏移量为:0x2857和0x2ae9
level11.1 还是老套路,这次没有符号了。依然可以gdb调试拿到偏移量:0x197b+1和0x1a5a。
为什么要+1?是因为通过ida pro打开源程序后,发现它是带符号的opcode,因此查阅后需要将OF 85改成OF 84,所以,需要+1修改后面那个字节的值。而后面那个偏移不需要+1因为它时不带符号的opcode。因此后面的偏移值改成74即可。
level12.0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 void __fastcall __noreturn execute_program (_BYTE *a1) int v1; int v2; size_t v3; char buf[136 ]; unsigned __int64 v6; 0x28u );0 , a1 + 67 , 6uLL ); 99 ] = 18 ;100 ] = -84 ;101 ] = -73 ;102 ] = -78 ;103 ] = -91 ;104 ] = 26 ;memcmp (a1 + 99 , a1 + 67 , 6uLL );0 ;if ( v1 )printf ("INCORRECT!" );else printf ("CORRECT! Your flag: " );"/flag" , 0 );0x64u LL);1 , buf, v3);exit (!v4);
将al数组=[18, -84, -73, -78, -91, -26]使用python中的struct.pack打包成字节序,然后发送给目标程序就行了。
1 2 3 4 5 6 7 8 9 from pwn import *'/challenge/babyrev-level-12-0' )18 , -84 , -73 , -78 , -91 , 26 ]'6b' , *al)print (payload)print (p.readall())
struct.pack说明:
1 struct.pack(fmt, v1, v2, ...)
fmt:格式字符串,指定如何将数据打包成二进制。格式字符串由字符组成,每个字符表示一种数据类型。v1,v2,...:要打包的数据,可以是整数、浮点数、字符串等。
格式字符串fmt由字节顺序(@,=,<,>,!)和数据类型(c,b,B,?,h,H,i,I,l,L,q,Q,f,d,s,p,x)组成。其中字节顺序可选,@默认,使用本地字节顺序、大小和对齐方式。=使用本地字节序,标准大小,无对其。<小端模式,>大端模式,!网络字节序(大端模式)。后续的数据类型常见的有:
c:字符;b:有符号字节;B:无符号字节;h:有符号短整型;H:无符号短整型;i:有符号整型;I:无符号整型;s:字符串,需要指定长度,例如10s表示10字节的字符串
level12.1 同理
1 2 3 4 5 6 7 8 9 from pwn import *'/challenge/babyrev-level-12-1' )61 ,118 ,-61 ,-110 ]'4b' , *al)print (payload)print (p.readall())
level13.0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 [s] IMM b = 0x71 0x1 0xbd STM *b = a # a1 [0x71 ] = 0xbd ADD b c0xb5 STM *b = a # a1 [0x72 ] = 0xb5 ADD b c0xd8 STM *b = a # a1 [0x73 ] = 0xd8 ADD b c0xdc STM *b = a # a1 [0x74 ] = 0xdc ADD b c0xbd STM *b = a # a1 [0x75 ] = 0xbd ADD b c0x98 STM *b = a # a1 [0x76 ] = 0x98 ADD b c
可以看到是一系列寄存器/立即数的操作。题目要求输入6个字节。 而上述正好是从a1[113]开始,写入了6个字节。因此,我们把这6个字节转换成字节序丢给它即可。
1 2 3 4 5 6 7 8 9 from pwn import *'/challenge/babyrev-level-13-0' )0xbd ,0xb5 ,0xd8 ,0xdc ,0xbd ,0x98 ]'6B' , *al)print (payload)print (p.readall())
level13.1 现在,题目不会打印出汇编伪代码了。就得自己通过ida 看出来。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 sub_1533 (a1, 1 LL, 91 LL); sub_1533 (a1, 8 LL, 1 LL); sub_1533 (a1, 2 LL, 70 LL); sub_1687 (a1, 1 LL, 2 LL); sub_1568 (a1, 1 LL, 8 LL); sub_1533 (a1, 2 LL, 236 LL);sub_1687 (a1, 1 LL, 2 LL);sub_1568 (a1, 1 LL, 8 LL);sub_1533 (a1, 2 LL, 45 LL);sub_1687 (a1, 1 LL, 2 LL);sub_1568 (a1, 1 LL, 8 LL);sub_1533 (a1, 2 LL, 101 LL);sub_1687 (a1, 1 LL, 2 LL);sub_1568 (a1, 1 LL, 8 LL);
看了看,要手工调出来得好久,还容易出错。还是写代码快:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 from pwn import *import numpy as np512 ,1 ), dtype=int )def sub_1533 (a2,a3 ):return sub_1415(a2,a3)def sub_1415 (a2, a3 ):match a2:case 2 :256 ] = a3case 1 :257 ] = a3case 8 :258 ] = a3case 32 :259 ] = a3case 4 :260 ] = a3 case 16 :261 ] = a3 case 64 :262 ] = a3 case _:print ("unknown register" )return resultdef sub_1687 (a2, a3 ):return sub_1507(v4, v3)def sub_1363 (a2 ):0 match a2:case 2 :return a1[256 ]case 1 :return a1[257 ]case 8 :return a1[258 ]case 32 :return a1[259 ]case 4 :return a1[260 ]case 16 :return a1[261 ]case 64 :return a1[262 ]def sub_1507 (a2, a3 ):return resdef sub_1568 (a2, a3 ):return sub_1415(a2, v3+v4)1 , 91 )8 , 1 )2 , 70 )1 , 2 )1 , 8 )2 , 236 )1 , 2 )1 , 8 )2 , 45 )1 , 2 )1 , 8 )2 , 101 )1 , 2 )1 , 8 )for i in range (4 ):print (a1[91 +i])
最后exp就是之前的模板:
1 2 3 4 5 6 7 8 9 from pwn import *'/challenge/babyrev-level-13-1' )70 ,236 ,45 ,101 ]'4B' , *al)print (payload)print (p.readall())
level14.0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 [s ] IMM b = 0x36 s ] IMM c = 0x6 s ] IMM a = 0 s ] SYS 0x2 as ] ... read_memorys ] ... return value (in register a): 0x2 s ] IMM b = 0x56 s ] IMM c = 0x1 s ] IMM a = 0x14 s ] STM *b = a # a1[0x56] = 0x14 s ] ADD b cs ] IMM a = 0xd2 s ] STM *b = a # a1[0x57] = 0xd2 s ] ADD b cs ] IMM a = 0xcf s ] STM *b = a # a1[0x58] = 0xcf s ] ADD b cs ] IMM a = 0x31 s ] STM *b = a # a1[0x59] = 0x31 s ] ADD b cs ] IMM a = 0x54 s ] STM *b = a # a1[0x5a] = 0x54 s ] ADD b cs ] IMM a = 0xb8 s ] STM *b = a # a1[0x5b] = 0xb8 s ] ADD b c
老规矩,第一关还是会打印出来。那么我们直接简单推导一下就行了。exp:
1 2 3 4 5 6 7 8 9 10 from pwn import *'/challenge/babyrev-level-14-0' )0x14 ,0xd2 ,0xcf ,0x31 ,0x54 ,0xb8 ]'6B' , *al)print (payload)print (p.readall())
level14.1 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 from pwn import *import numpy as np512 ,1 ), dtype=int )def sub_1533 (a2,a3 ):return sub_1415(a2,a3)def sub_1415 (a2, a3 ):match a2:case 2 :256 ] = a3case 1 :257 ] = a3case 8 :258 ] = a3case 32 :259 ] = a3case 4 :260 ] = a3 case 16 :261 ] = a3 case 64 :262 ] = a3 case _:print ("unknown register" )return resultdef sub_1687 (a2, a3 ):return sub_1507(v4, v3)def sub_1363 (a2 ):0 match a2:case 2 :return a1[256 ]case 1 :return a1[257 ]case 8 :return a1[258 ]case 32 :return a1[259 ]case 4 :return a1[260 ]case 16 :return a1[261 ]case 64 :return a1[262 ]def sub_1507 (a2, a3 ):return resdef sub_1568 (a2, a3 ):return sub_1415(a2, v3+v4)16 , 114 )2 , 1 )8 , 97 )16 , 8 )16 , 2 )8 , 170 )16 , 8 )16 , 2 )8 , 239 )16 , 8 )16 , 2 )8 , 133 )16 , 8 )16 , 2 )8 , 167 )16 , 8 )16 , 2 )8 , 205 )16 , 8 )16 , 2 )8 , 70 )16 , 8 )16 , 2 )8 , 226 )16 , 8 )16 , 2 )for i in range (8 ):print (a1[114 +i])
这里能够注释掉前面几个混淆,因为没起作用。后面的sub_18969()是获取用户输入的。所以不需要写。
最后exp就不贴了,模板还是之前的,然后改一改数字就行了。
level15.0 道理是一样的,不过这一关的open flag啥的也被做成了函数,也就是后面的if()语句内的。我们只需要关注memcmp()函数以前的vmcode即可。
level15.1 还是之前的脚本,跑一下,打印出来的整数转成字节序,发给目标程序即可拿到flag。
level16.0 1 0x5c , 0 x99, 0 xc6, 0 x21, 0 xce, 0 xf2, 0 x7e, 0 xb8
依然不用管后续的cmp就行了。其实就是刚开始的cmp换了种形式。依然可以直接按照先前的方法。记住ida pro这种形式,其实也是一种字符串的匹配问题。
level16.1 这一关就记住,找到输入的位置。根据之前的规律,很简单就知道用户从a1的哪个索引处开始写入数据的:
因此,我们只需要用之前的脚本执行一下就行。(可能有名字的差异,但是大差不差。简单找一找就能知道对应的函数了)
level17.0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 [s] IMM b = 0x51 0x1 0x87 STM *b = a # a1 [81 ] = 0x87 ADD b c0xf STM *b = a # a1 [82 ] = 0xf ADD b c0xca STM *b = a # 83 ADD b c0xc1 STM *b = a # 84 ADD b c0xde STM *b = a # 85 ADD b c0x29 STM *b = a # 86 ADD b cb = 0x31 0x1 LDM a = *b # a = a1 [0x31 ]0xc0 # d = 0xc0 ADD a d # a = a1 [0x31 ] + 0xc0 STM *b = a # a1 [0x31 ] = 0xc0 ADD b c # b = 0x31 + 0x32 LDM a = *b # a = a1 [0x32 ]0 ADD a d # a = a1 [0x32 ] + 0
可以发现,多了LDM指令。经过分析之后,发现它是会对我们的输入进行了一个加法的操作。所以,我们把它打印出来,然后做减法就行了。注意转换成字节序的时候,有符号和范围溢出的问题。我们可以分开处理正数和负数就行了。exp:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 from pwn import *
level17.1 这里记录一下题目中的api,方便我们拿到匹配的字符串。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 from pwn import *import numpy as np512 ,1 ), dtype=int )def imm (a2,a3 ):return sub_1415(a2,a3)def stm (a2, a3 ):return write_memory(v4, v3)def write_memory (a2, a3 ):return resdef add (a2, a3 ):return sub_1415(a2, v3+v4)def read_register (a2 ):match a2:case 4 :return a1[257 ]case 16 :return a1[256 ]case 64 :return a1[261 ]case 1 :return a1[259 ]case 32 :return a1[260 ]case 2 :return a1[258 ]return a1[262 ]def write_register (a2, a3 ): match a2:case 4 :257 ] = a3case 16 :256 ] = a3case 8 :262 ] = a3case 64 :261 ] = a3case 1 :259 ] = a3case 32 :260 ] = a3case 2 :258 ] = a3def ldm (a2, a3 ):return write_register(a2, memory)def read_memory (a2 ):return a1[a2]def imm (a2, a3 ):return write_register(a2, a3)def write_memory (a2, a3 ):def stm (a2, a3 ): return write_memory(v5, v3) def add (a2, a3 ):return write_register(a2, v3+v5)
ida打开,同样的有LDM指令,不过符号没有标识出来而已。然后发现它是在它原先的字符串上进行了加法,而不是上一题那样在我们输入的字符串上进行加法。那就很简单了。只需要把最后的值打印出来,然后大于256的减一下就行了。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 from pwn import *'/challenge/babyrev-level-17-1' )188 , 371 , 259 , 201 ,273 ,381 , 204 , 259 ,313 , 219 , 235 ,411 ]b'' for i in range (len (al)):if al[i] > 256 :'B' , al[i] - 256 )else :'B' , al[i])print (payload)print (p.readall())
level18.0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 [s] IMM b = 0x6d 0x1 0x81 STM *b = a ADD b c0xea STM *b = aADD b c0x34 STM *b = aADD b c0xde STM *b = aADD b c0xf2 STM *b = aADD b c0x1d STM *b = aADD b c0xe STM *b = aADD b c0x49 STM *b = aADD b c0xe1 STM *b = aADD b cb = 0x6d LDM b = *b # b = a1 [0x6d ] = 0x81 0x4d LDM a = *a # a = a1 [0x4d ] users input from 0x4d 0x2e ADD a c # a = 0x2e CMP a b # cmp a1 [0x6d ], a1 [0x4d ] + 0x2e b = 0x6e LDM b = *b 0x4e LDM a = *a0xa7 ADD a cCMP a b b = 0x6f LDM b = *b 0x4f LDM a = *a0x9e ADD a cCMP a b b = 0x70 LDM b = *b 0x50 LDM a = *a0x82 ADD a cCMP a b b = 0x71 LDM b = *b 0x51 LDM a = *a0x9d ADD a cCMP a b b = 0x72 LDM b = *b 0x52 LDM a = *a0x89 ADD a cCMP a b b = 0x73 LDM b = *b 0x53 LDM a = *a0xdc ADD a cCMP a b b = 0x74 LDM b = *b 0x54 LDM a = *a0x7 ADD a cCMP a b b = 0x75 LDM b = *b 0x55 LDM a = *a0xa9 ADD a cCMP a b
其他的不怎么用改,只不过在这里需要自己加变量,然后打印出来中间的输入。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 imm(0x20, 0x4D)*b = aadd (0x20, 0x40) # [s] ADD b cadd (0x20, 0x40)add (0x20, 0x40)add (0x20, 0x40)add (0x20, 0x40)add (0x20, 0x40)add (0x20, 0x40)add (0x20, 0x40)add (0x20, 0x40) # [s] ADD b c*b *a add (2, 0x40) # [s] add a c add (1, 0x10) # [s] add s dadd (2, 0x40)add (1, 0x10) # [s] add s dadd (2, 0x40)add (1, 0x10) # [s] add s dadd (2, 0x40)add (1, 0x10) # [s] add s dadd (2, 0x40)add (1, 0x10) # [s] add s dadd (2, 0x40)add (1, 0x10) # [s] add s dadd (2, 0x40)add (1, 0x10) # [s] add s dadd (2, 0x40)add (1, 0x10) # [s] add s dadd (2, 0x40)add (1, 0x10) # [s] add s dprint (a1[0x6d: 0x6d + 9])print (a1[0x4d: 0x4d + 9])for i in range(9):print (a1[:9])
根据描述可以知道寄存器a,b,c,d,s,i,f分别是哪些16进制数代表的。所以就可以用上去,把中间值存起来,最后做一个减法就行了。
最后记得一点,就是有一个小于-128的负数,我们加上256,而不是加128。因为原本的数是因为大于256才溢出成为负数的。那么同理,减法也是减去256而不是128。
level18.1 从a1[121]接收用户输入,目标字符串在a1[153];从逻辑上很容易看出来,这道题是在目标字符串上加了一个数。所以,这里我们需要修改上题的逻辑,把加之后的数据依然保存在原来的a1[153]开始的连续地址处就行了。最后再打印出来,转成字节序发送即可。
level19.0 原来,这里才开始是vmcode啊。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 220 221 222 223 224 225 226 227 228 229 230 231 232 233 234 235 236 237 238 239 [V] a :0 b :0 c:0 d:0 s:0 i :0 x1 f:0 [I] op:0 x20 arg1:0 x1 arg2:0 x52 [s] IMM d = 0 x52[V] a :0 b :0 c:0 d:0 x52 s:0 i :0 x2 f:0 [I] op:0 x4 arg1:0 x20 arg2:0 x1 [s] STK i d[s] ... pushing d [s] ... popping i [V] a :0 b :0 c:0 d:0 x52 s:0 i :0 x53 f:0 [I] op:0 x20 arg1:0 x1 arg2:0 x6a[s] IMM d = 0 x6a[V] a :0 b :0 c:0 d:0 x6a s:0 i :0 x54 f:0 [I] op:0 x20 arg1:0 x8 arg2:0 x9c[s] IMM c = 0 x9c[V] a :0 b :0 c:0 x9c d:0 x6a s:0 i :0 x55 f:0 [I] op:0 x8 arg1:0 x8 arg2:0 x1[s] STM *c = d [V] a :0 b :0 c:0 x9c d:0 x6a s:0 i :0 x56 f:0 [I] op:0 x20 arg1:0 x1 arg2:0 x39[s] IMM d = 0 x39 [V] a :0 b :0 c:0 x9c d:0 x39 s:0 i :0 x57 f:0 [I] op:0 x20 arg1:0 x8 arg2:0 x9d[s] IMM c = 0 x9d[V] a :0 b :0 c:0 x9d d:0 x39 s:0 i :0 x58 f:0 [I] op:0 x8 arg1:0 x8 arg2:0 x1[s] STM *c = d [V] a :0 b :0 c:0 x9d d:0 x39 s:0 i :0 x59 f:0 [I] op:0 x20 arg1:0 x1 arg2:0 xf2[s] IMM d = 0 xf2[V] a :0 b :0 c:0 x9d d:0 xf2 s:0 i :0 x5a f:0 [I] op:0 x20 arg1:0 x8 arg2:0 x9e[s] IMM c = 0 x9e[V] a :0 b :0 c:0 x9e d:0 xf2 s:0 i :0 x5b f:0 [I] op:0 x8 arg1:0 x8 arg2:0 x1[s] STM *c = d[V] a :0 b :0 c:0 x9e d:0 xf2 s:0 i :0 x5c f:0 [I] op:0 x20 arg1:0 x1 arg2:0 x34[s] IMM d = 0 x34[V] a :0 b :0 c:0 x9e d:0 x34 s:0 i :0 x5d f:0 [I] op:0 x20 arg1:0 x8 arg2:0 x9f[s] IMM c = 0 x9f[V] a :0 b :0 c:0 x9f d:0 x34 s:0 i :0 x5e f:0 [I] op:0 x8 arg1:0 x8 arg2:0 x1[s] STM *c = d[V] a :0 b :0 c:0 x9f d:0 x34 s:0 i :0 x5f f:0 [I] op:0 x20 arg1:0 x1 arg2:0 x50[s] IMM d = 0 x50[V] a :0 b :0 c:0 x9f d:0 x50 s:0 i :0 x60 f:0 [I] op:0 x20 arg1:0 x8 arg2:0 xa0[s] IMM c = 0 xa0[V] a :0 b :0 c:0 xa0 d:0 x50 s:0 i :0 x61 f:0 [I] op:0 x8 arg1:0 x8 arg2:0 x1[s] STM *c = d[V] a :0 b :0 c:0 xa0 d:0 x50 s:0 i :0 x62 f:0 [I] op:0 x20 arg1:0 x1 arg2:0 x39[s] IMM d = 0 x39[V] a :0 b :0 c:0 xa0 d:0 x39 s:0 i :0 x63 f:0 [I] op:0 x20 arg1:0 x8 arg2:0 xa1[s] IMM c = 0 xa1[V] a :0 b :0 c:0 xa1 d:0 x39 s:0 i :0 x64 f:0 [I] op:0 x8 arg1:0 x8 arg2:0 x1[s] STM *c = d[V] a :0 b :0 c:0 xa1 d:0 x39 s:0 i :0 x65 f:0 [I] op:0 x20 arg1:0 x1 arg2:0 x38[s] IMM d = 0 x38[V] a :0 b :0 c:0 xa1 d:0 x38 s:0 i :0 x66 f:0 [I] op:0 x20 arg1:0 x8 arg2:0 xa2[s] IMM c = 0 xa2[V] a :0 b :0 c:0 xa2 d:0 x38 s:0 i :0 x67 f:0 [I] op:0 x8 arg1:0 x8 arg2:0 x1[s] STM *c = d[V] a :0 b :0 c:0 xa2 d:0 x38 s:0 i :0 x68 f:0 [I] op:0 x20 arg1:0 x1 arg2:0 xbf[s] IMM d = 0 xbf[V] a :0 b :0 c:0 xa2 d:0 xbf s:0 i :0 x69 f:0 [I] op:0 x20 arg1:0 x8 arg2:0 xa3[s] IMM c = 0 xa3[V] a :0 b :0 c:0 xa3 d:0 xbf s:0 i :0 x6a f:0 [I] op:0 x8 arg1:0 x8 arg2:0 x1[s] STM *c = d[V] a :0 b :0 c:0 xa3 d:0 xbf s:0 i :0 x6b f:0 [I] op:0 x20 arg1:0 x1 arg2:0 xee[s] IMM d = 0 xee[V] a :0 b :0 c:0 xa3 d:0 xee s:0 i :0 x6c f:0 [I] op:0 x20 arg1:0 x8 arg2:0 xa4[s] IMM c = 0 xa4[V] a :0 b :0 c:0 xa4 d:0 xee s:0 i :0 x6d f:0 [I] op:0 x8 arg1:0 x8 arg2:0 x1[s] STM *c = d[V] a :0 b :0 c:0 xa4 d:0 xee s:0 i :0 x6e f:0 [I] op:0 x20 arg1:0 x1 arg2:0 xd8[s] IMM d = 0 xd8[V] a :0 b :0 c:0 xa4 d:0 xd8 s:0 i :0 x6f f:0 [I] op:0 x20 arg1:0 x8 arg2:0 xa5[s] IMM c = 0 xa5[V] a :0 b :0 c:0 xa5 d:0 xd8 s:0 i :0 x70 f:0 [I] op:0 x8 arg1:0 x8 arg2:0 x1[s] STM *c = d[V] a :0 b :0 c:0 xa5 d:0 xd8 s:0 i :0 x71 f:0 [I] op:0 x20 arg1:0 x1 arg2:0 x65[s] IMM d = 0 x65[V] a :0 b :0 c:0 xa5 d:0 x65 s:0 i :0 x72 f:0 [I] op:0 x20 arg1:0 x8 arg2:0 xa6[s] IMM c = 0 xa6[V] a :0 b :0 c:0 xa6 d:0 x65 s:0 i :0 x73 f:0 [I] op:0 x8 arg1:0 x8 arg2:0 x1[s] STM *c = d[V] a :0 b :0 c:0 xa6 d:0 x65 s:0 i :0 x74 f:0 [I] op:0 x20 arg1:0 x1 arg2:0 xe0[s] IMM d = 0 xe0[V] a :0 b :0 c:0 xa6 d:0 xe0 s:0 i :0 x75 f:0 [I] op:0 x20 arg1:0 x8 arg2:0 xa7[s] IMM c = 0 xa7[V] a :0 b :0 c:0 xa7 d:0 xe0 s:0 i :0 x76 f:0 [I] op:0 x8 arg1:0 x8 arg2:0 x1[s] STM *c = d[V] a :0 b :0 c:0 xa7 d:0 xe0 s:0 i :0 x77 f:0 [I] op:0 x20 arg1:0 x1 arg2:0 x15[s] IMM d = 0 x15[V] a :0 b :0 c:0 xa7 d:0 x15 s:0 i :0 x78 f:0 [I] op:0 x20 arg1:0 x8 arg2:0 xa8[s] IMM c = 0 xa8[V] a :0 b :0 c:0 xa8 d:0 x15 s:0 i :0 x79 f:0 [I] op:0 x8 arg1:0 x8 arg2:0 x1[s] STM *c = d[V] a :0 b :0 c:0 xa8 d:0 x15 s:0 i :0 x7a f:0 [I] op:0 x20 arg1:0 x1 arg2:0 x6b[s] IMM d = 0 x6b[V] a :0 b :0 c:0 xa8 d:0 x6b s:0 i :0 x7b f:0 [I] op:0 x20 arg1:0 x8 arg2:0 xa9[s] IMM c = 0 xa9[V] a :0 b :0 c:0 xa9 d:0 x6b s:0 i :0 x7c f:0 [I] op:0 x8 arg1:0 x8 arg2:0 x1[s] STM *c = d [V] a :0 b :0 c:0 xa9 d:0 x6b s:0 i :0 x7d f:0 [I] op:0 x20 arg1:0 x20 arg2:0 x8a[s] IMM i = 0 x8a[V] a :0 b :0 c:0 xa9 d:0 x6b s:0 i :0 x8b f:0 [I] op:0 x4 arg1:0 arg2:0 x4[s] STK NONE a [s] ... pushing a [V] a :0 b :0 c:0 xa9 d:0 x6b s:0 x1 i :0 x8c f:0 [I] op:0 x4 arg1:0 arg2:0 x2[s] STK NONE b [s] ... pushing b [V] a :0 b :0 c:0 xa9 d:0 x6b s:0 x2 i :0 x8d f:0 [I] op:0 x4 arg1:0 arg2:0 x8[s] STK NONE c[s] ... pushing c [V] a :0 b :0 c:0 xa9 d:0 x6b s:0 x3 i :0 x8e f:0 [I] op:0 x20 arg1:0 x2 arg2:0 x1[s] IMM b = 0 x1[V] a :0 b :0 x1 c:0 xa9 d:0 x6b s:0 x3 i :0 x8f f:0 [I] op:0 x10 arg1:0 x2 arg2:0 x40[s] ADD b s[V] a :0 b :0 x4 c:0 xa9 d:0 x6b s:0 x3 i :0 x90 f:0 [I] op:0 x20 arg1:0 x1 arg2:0 x4b[s] IMM d = 0 x4b[V] a :0 b :0 x4 c:0 xa9 d:0 x4b s:0 x3 i :0 x91 f:0 [I] op:0 x4 arg1:0 arg2:0 x1[s] STK NONE d[s] ... pushing d [V] a :0 b :0 x4 c:0 xa9 d:0 x4b s:0 x4 i :0 x92 f:0 [I] op:0 x20 arg1:0 x1 arg2:0 x45[s] IMM d = 0 x45[V] a :0 b :0 x4 c:0 xa9 d:0 x45 s:0 x4 i :0 x93 f:0 [I] op:0 x4 arg1:0 arg2:0 x1[s] STK NONE d[s] ... pushing d [V] a :0 b :0 x4 c:0 xa9 d:0 x45 s:0 x5 i :0 x94 f:0 [I] op:0 x20 arg1:0 x1 arg2:0 x59[s] IMM d = 0 x59[V] a :0 b :0 x4 c:0 xa9 d:0 x59 s:0 x5 i :0 x95 f:0 [I] op:0 x4 arg1:0 arg2:0 x1[s] STK NONE d[s] ... pushing d [V] a :0 b :0 x4 c:0 xa9 d:0 x59 s:0 x6 i :0 x96 f:0 [I] op:0 x20 arg1:0 x1 arg2:0 x3a[s] IMM d = 0 x3a[V] a :0 b :0 x4 c:0 xa9 d:0 x3a s:0 x6 i :0 x97 f:0 [I] op:0 x4 arg1:0 arg2:0 x1[s] STK NONE d[s] ... pushing d [V] a :0 b :0 x4 c:0 xa9 d:0 x3a s:0 x7 i :0 x98 f:0 [I] op:0 x20 arg1:0 x1 arg2:0 x20[s] IMM d = 0 x20[V] a :0 b :0 x4 c:0 xa9 d:0 x20 s:0 x7 i :0 x99 f:0 [I] op:0 x4 arg1:0 arg2:0 x1[s] STK NONE d[s] ... pushing d [V] a :0 b :0 x4 c:0 xa9 d:0 x20 s:0 x8 i :0 x9a f:0 [I] op:0 x20 arg1:0 x8 arg2:0 x5[s] IMM c = 0 x5[V] a :0 b :0 x4 c:0 x5 d:0 x20 s:0 x8 i :0 x9b f:0 [I] op:0 x20 arg1:0 x4 arg2:0 x1[s] IMM a = 0 x1[V] a :0 x1 b :0 x4 c:0 x5 d:0 x20 s:0 x8 i :0 x9c f:0 [I] op:0 x1 arg1:0 x8 arg2:0 x1[s] SYS 0 x8 d[s] ... write[s] ... return value (in register d): 0 x5[V] a :0 x1 b :0 x4 c:0 x5 d:0 x5 s:0 x8 i :0 x9d f:0 [I] op:0 x4 arg1:0 x8 arg2:0 [s] STK c NONE[s] ... popping c [V] a :0 x1 b :0 x4 c:0 x20 d:0 x5 s:0 x7 i :0 x9e f:0 [I] op:0 x4 arg1:0 x2 arg2:0 [s] STK b NONE[s] ... popping b [V] a :0 x1 b :0 x3a c:0 x20 d:0 x5 s:0 x6 i :0 x9f f:0 [I] op:0 x4 arg1:0 x4 arg2:0 [s] STK a NONE[s] ... popping a [V] a :0 x59 b :0 x3a c:0 x20 d:0 x5 s:0 x5 i :0 xa0 f:0 [I] op:0 x4 arg1:0 arg2:0 x4[s] STK NONE a [s] ... pushing a [V] a :0 x59 b :0 x3a c:0 x20 d:0 x5 s:0 x6 i :0 xa1 f:0 [I] op:0 x4 arg1:0 arg2:0 x2[s] STK NONE b [s] ... pushing b [V] a :0 x59 b :0 x3a c:0 x20 d:0 x5 s:0 x7 i :0 xa2 f:0 [I] op:0 x4 arg1:0 arg2:0 x8[s] STK NONE c[s] ... pushing c [V] a :0 x59 b :0 x3a c:0 x20 d:0 x5 s:0 x8 i :0 xa3 f:0 [I] op:0 x20 arg1:0 x2 arg2:0 x30[s] IMM b = 0 x30[V] a :0 x59 b :0 x30 c:0 x20 d:0 x5 s:0 x8 i :0 xa4 f:0 [I] op:0 x20 arg1:0 x8 arg2:0 xe[s] IMM c = 0 xe[V] a :0 x59 b :0 x30 c:0 xe d:0 x5 s:0 x8 i :0 xa5 f:0 [I] op:0 x20 arg1:0 x4 arg2:0 [s] IMM a = 0 [V] a :0 b :0 x30 c:0 xe d:0 x5 s:0 x8 i :0 xa6 f:0 [I] op:0 x1 arg1:0 x4 arg2:0 x1[s] SYS 0 x4 d[s] ... read_memory1
上面的是接受用户输入前的代码,下面的是接收用户输入后的处理逻辑。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 220 221 222 223 224 225 226 227 228 229 230 231 232 233 234 235 236 237 238 239 240 241 242 243 [s] ... return value (in register d): 0 x2[V] a :0 b :0 x30 c:0 xe d:0 x2 s:0 x8 i :0 xa7 f:0 [I] op:0 x4 arg1:0 x8 arg2:0 [s] STK c NONE[s] ... popping c [V] a :0 b :0 x30 c:0 x20 d:0 x2 s:0 x7 i :0 xa8 f:0 [I] op:0 x4 arg1:0 x2 arg2:0 [s] STK b NONE[s] ... popping b [V] a :0 b :0 x3a c:0 x20 d:0 x2 s:0 x6 i :0 xa9 f:0 [I] op:0 x4 arg1:0 x4 arg2:0 [s] STK a NONE[s] ... popping a [V] a :0 x59 b :0 x3a c:0 x20 d:0 x2 s:0 x5 i :0 xaa f:0 [I] op:0 x20 arg1:0 x20 arg2:0 xaa[s] IMM i = 0 xaa [V] a :0 x59 b :0 x3a c:0 x20 d:0 x2 s:0 x5 i :0 xab f:0 [I] op:0 x4 arg1:0 arg2:0 x4[s] STK NONE a [s] ... pushing a [V] a :0 x59 b :0 x3a c:0 x20 d:0 x2 s:0 x6 i :0 xac f:0 [I] op:0 x4 arg1:0 arg2:0 x2[s] STK NONE b [s] ... pushing b [V] a :0 x59 b :0 x3a c:0 x20 d:0 x2 s:0 x7 i :0 xad f:0 [I] op:0 x4 arg1:0 arg2:0 x8[s] STK NONE c[s] ... pushing c [V] a :0 x59 b :0 x3a c:0 x20 d:0 x2 s:0 x8 i :0 xae f:0 [I] op:0 x4 arg1:0 x8 arg2:0 [s] STK c NONE[s] ... popping c[V] a :0 x59 b :0 x3a c:0 x20 d:0 x2 s:0 x7 i :0 xaf f:0 [I] op:0 x4 arg1:0 x2 arg2:0 [s] STK b NONE[s] ... popping b [V] a :0 x59 b :0 x3a c:0 x20 d:0 x2 s:0 x6 i :0 xb0 f:0 [I] op:0 x4 arg1:0 x4 arg2:0 [s] STK a NONE[s] ... popping a [V] a :0 x59 b :0 x3a c:0 x20 d:0 x2 s:0 x5 i :0 xb1 f:0 [I] op:0 x20 arg1:0 x20 arg2:0 x7d[s] IMM i = 0 x7d[V] a :0 x59 b :0 x3a c:0 x20 d:0 x2 s:0 x5 i :0 x7e f:0 [I] op:0 x20 arg1:0 x4 arg2:0 x30[s] IMM a = 0 x30[V] a :0 x30 b :0 x3a c:0 x20 d:0 x2 s:0 x5 i :0 x7f f:0 [I] op:0 x20 arg1:0 x2 arg2:0 x9e[s] IMM b = 0 x9e[V] a :0 x30 b :0 x9e c:0 x20 d:0 x2 s:0 x5 i :0 x80 f:0 [I] op:0 x20 arg1:0 x8 arg2:0 xc[s] IMM c = 0 xc[V] a :0 x30 b :0 x9e c:0 xc d:0 x2 s:0 x5 i :0 x81 f:0 [I] op:0 x20 arg1:0 x1 arg2:0 x2[s] IMM d = 0 x2[V] a :0 x30 b :0 x9e c:0 xc d:0 x2 s:0 x5 i :0 x82 f:0 [I] op:0 x10 arg1:0 x1 arg2:0 x20[s] ADD d i [V] a :0 x30 b :0 x9e c:0 xc d:0 x84 s:0 x5 i :0 x83 f:0 [I] op:0 x4 arg1:0 arg2:0 x1[s] STK NONE d[s] ... pushing d [V] a :0 x30 b :0 x9e c:0 xc d:0 x84 s:0 x6 i :0 x84 f:0 [I] op:0 x20 arg1:0 x20 arg2:0 xce[s] IMM i = 0 xce[V] a :0 x30 b :0 x9e c:0 xc d:0 x84 s:0 x6 i :0 xcf f:0 [I] op:0 x10 arg1:0 x4 arg2:0 x8[s] ADD a c[V] a :0 x3c b :0 x9e c:0 xc d:0 x84 s:0 x6 i :0 xd0 f:0 [I] op:0 x10 arg1:0 x2 arg2:0 x8[s] ADD b c[V] a :0 x3c b :0 xaa c:0 xc d:0 x84 s:0 x6 i :0 xd1 f:0 [I] op:0 x20 arg1:0 x1 arg2:0 xff[s] IMM d = 0 xff[V] a :0 x3c b :0 xaa c:0 xc d:0 xff s:0 x6 i :0 xd2 f:0 [I] op:0 x10 arg1:0 x4 arg2:0 x1[s] ADD a d[V] a :0 x3b b :0 xaa c:0 xc d:0 xff s:0 x6 i :0 xd3 f:0 [I] op:0 x10 arg1:0 x2 arg2:0 x1[s] ADD b d[V] a :0 x3b b :0 xa9 c:0 xc d:0 xff s:0 x6 i :0 xd4 f:0 [I] op:0 x4 arg1:0 arg2:0 x4[s] STK NONE a [s] ... pushing a [V] a :0 x3b b :0 xa9 c:0 xc d:0 xff s:0 x7 i :0 xd5 f:0 [I] op:0 x4 arg1:0 arg2:0 x2[s] STK NONE b [s] ... pushing b [V] a :0 x3b b :0 xa9 c:0 xc d:0 xff s:0 x8 i :0 xd6 f:0 [I] op:0 x2 arg1:0 x4 arg2:0 x4[s] LDM a = *a [V] a :0 b :0 xa9 c:0 xc d:0 xff s:0 x8 i :0 xd7 f:0 [I] op:0 x2 arg1:0 x2 arg2:0 x2[s] LDM b = *b [V] a :0 b :0 x6b c:0 xc d:0 xff s:0 x8 i :0 xd8 f:0 [I] op:0 x80 arg1:0 x4 arg2:0 x2[s] CMP a b [V] a :0 b :0 x6b c:0 xc d:0 xff s:0 x8 i :0 xd9 f:0 xc[I] op:0 x4 arg1:0 x2 arg2:0 [s] STK b NONE[s] ... popping b [V] a :0 b :0 xa9 c:0 xc d:0 xff s:0 x7 i :0 xda f:0 xc[I] op:0 x4 arg1:0 x4 arg2:0 [s] STK a NONE[s] ... popping a [V] a :0 x3b b :0 xa9 c:0 xc d:0 xff s:0 x6 i :0 xdb f:0 xc[I] op:0 x20 arg1:0 x1 arg2:0 xe2[s] IMM d = 0 xe2[V] a :0 x3b b :0 xa9 c:0 xc d:0 xe2 s:0 x6 i :0 xdc f:0 xc[I] op:0 x40 arg1:0 x4 arg2:0 x1[j] JMP N d[j] ... TAKEN[V] a :0 x3b b :0 xa9 c:0 xc d:0 xe2 s:0 x6 i :0 xe3 f:0 xc[I] op:0 x4 arg1:0 x1 arg2:0 x8[s] STK d c[s] ... pushing c[s] ... popping d[V] a :0 x3b b :0 xa9 c:0 xc d:0 xc s:0 x6 i :0 xe4 f:0 xc[I] op:0 x4 arg1:0 x20 arg2:0 [s] STK i NONE[s] ... popping i [V] a :0 x3b b :0 xa9 c:0 xc d:0 xc s:0 x5 i :0 x85 f:0 xc[I] op:0 x20 arg1:0 x8 arg2:0 [s] IMM c = 0 [V] a :0 x3b b :0 xa9 c:0 d:0 xc s:0 x5 i :0 x86 f:0 xc[I] op:0 x80 arg1:0 x1 arg2:0 x8[s] CMP d c[V] a :0 x3b b :0 xa9 c:0 d:0 xc s:0 x5 i :0 x87 f:0 x6[I] op:0 x20 arg1:0 x1 arg2:0 x2[s] IMM d = 0 x2[V] a :0 x3b b :0 xa9 c:0 d:0 x2 s:0 x5 i :0 x88 f:0 x6[I] op:0 x40 arg1:0 x10 arg2:0 x1[j] JMP E d[j] ... NOT TAKEN[V] a :0 x3b b :0 xa9 c:0 d:0 x2 s:0 x5 i :0 x89 f:0 x6[I] op:0 x20 arg1:0 x1 arg2:0 xb1[s] IMM d = 0 xb1[V] a :0 x3b b :0 xa9 c:0 d:0 xb1 s:0 x5 i :0 x8a f:0 x6[I] op:0 x40 arg1:0 xa arg2:0 x1[j] JMP LG d[j] ... TAKEN[V] a :0 x3b b :0 xa9 c:0 d:0 xb1 s:0 x5 i :0 xb2 f:0 x6[I] op:0 x20 arg1:0 x2 arg2:0 x1[s] IMM b = 0 x1[V] a :0 x3b b :0 x1 c:0 d:0 xb1 s:0 x5 i :0 xb3 f:0 x6[I] op:0 x10 arg1:0 x2 arg2:0 x40[s] ADD b s[V] a :0 x3b b :0 x6 c:0 d:0 xb1 s:0 x5 i :0 xb4 f:0 x6[I] op:0 x20 arg1:0 x1 arg2:0 x49[s] IMM d = 0 x49[V] a :0 x3b b :0 x6 c:0 d:0 x49 s:0 x5 i :0 xb5 f:0 x6[I] op:0 x4 arg1:0 arg2:0 x1[s] STK NONE d[s] ... pushing d[V] a :0 x3b b :0 x6 c:0 d:0 x49 s:0 x6 i :0 xb6 f:0 x6[I] op:0 x20 arg1:0 x1 arg2:0 x4e[s] IMM d = 0 x4e[V] a :0 x3b b :0 x6 c:0 d:0 x4e s:0 x6 i :0 xb7 f:0 x6[I] op:0 x4 arg1:0 arg2:0 x1[s] STK NONE d[s] ... pushing d[V] a :0 x3b b :0 x6 c:0 d:0 x4e s:0 x7 i :0 xb8 f:0 x6[I] op:0 x20 arg1:0 x1 arg2:0 x43[s] IMM d = 0 x43[V] a :0 x3b b :0 x6 c:0 d:0 x43 s:0 x7 i :0 xb9 f:0 x6[I] op:0 x4 arg1:0 arg2:0 x1[s] STK NONE d[s] ... pushing d[V] a :0 x3b b :0 x6 c:0 d:0 x43 s:0 x8 i :0 xba f:0 x6[I] op:0 x20 arg1:0 x1 arg2:0 x4f[s] IMM d = 0 x4f[V] a :0 x3b b :0 x6 c:0 d:0 x4f s:0 x8 i :0 xbb f:0 x6[I] op:0 x4 arg1:0 arg2:0 x1[s] STK NONE d[s] ... pushing d[V] a :0 x3b b :0 x6 c:0 d:0 x4f s:0 x9 i :0 xbc f:0 x6[I] op:0 x20 arg1:0 x1 arg2:0 x52[s] IMM d = 0 x52[V] a :0 x3b b :0 x6 c:0 d:0 x52 s:0 x9 i :0 xbd f:0 x6[I] op:0 x4 arg1:0 arg2:0 x1[s] STK NONE d[s] ... pushing d[V] a :0 x3b b :0 x6 c:0 d:0 x52 s:0 xa i :0 xbe f:0 x6[I] op:0 x20 arg1:0 x1 arg2:0 x52[s] IMM d = 0 x52[V] a :0 x3b b :0 x6 c:0 d:0 x52 s:0 xa i :0 xbf f:0 x6[I] op:0 x4 arg1:0 arg2:0 x1[s] STK NONE d[s] ... pushing d[V] a :0 x3b b :0 x6 c:0 d:0 x52 s:0 xb i :0 xc0 f:0 x6[I] op:0 x20 arg1:0 x1 arg2:0 x45[s] IMM d = 0 x45[V] a :0 x3b b :0 x6 c:0 d:0 x45 s:0 xb i :0 xc1 f:0 x6[I] op:0 x4 arg1:0 arg2:0 x1[s] STK NONE d[s] ... pushing d[V] a :0 x3b b :0 x6 c:0 d:0 x45 s:0 xc i :0 xc2 f:0 x6[I] op:0 x20 arg1:0 x1 arg2:0 x43[s] IMM d = 0 x43[V] a :0 x3b b :0 x6 c:0 d:0 x43 s:0 xc i :0 xc3 f:0 x6[I] op:0 x4 arg1:0 arg2:0 x1[s] STK NONE d[s] ... pushing d[V] a :0 x3b b :0 x6 c:0 d:0 x43 s:0 xd i :0 xc4 f:0 x6[I] op:0 x20 arg1:0 x1 arg2:0 x54[s] IMM d = 0 x54[V] a :0 x3b b :0 x6 c:0 d:0 x54 s:0 xd i :0 xc5 f:0 x6[I] op:0 x4 arg1:0 arg2:0 x1[s] STK NONE d[s] ... pushing d[V] a :0 x3b b :0 x6 c:0 d:0 x54 s:0 xe i :0 xc6 f:0 x6[I] op:0 x20 arg1:0 x1 arg2:0 x21[s] IMM d = 0 x21[V] a :0 x3b b :0 x6 c:0 d:0 x21 s:0 xe i :0 xc7 f:0 x6[I] op:0 x4 arg1:0 arg2:0 x1[s] STK NONE d[s] ... pushing d[V] a :0 x3b b :0 x6 c:0 d:0 x21 s:0 xf i :0 xc8 f:0 x6[I] op:0 x20 arg1:0 x1 arg2:0 xa[s] IMM d = 0 xa[V] a :0 x3b b :0 x6 c:0 d:0 xa s:0 xf i :0 xc9 f:0 x6[I] op:0 x4 arg1:0 arg2:0 x1[s] STK NONE d[s] ... pushing d[V] a :0 x3b b :0 x6 c:0 d:0 xa s:0 x10 i :0 xca f:0 x6[I] op:0 x20 arg1:0 x8 arg2:0 xb[s] IMM c = 0 xb[V] a :0 x3b b :0 x6 c:0 xb d:0 xa s:0 x10 i :0 xcb f:0 x6[I] op:0 x20 arg1:0 x4 arg2:0 x1[s] IMM a = 0 x1[V] a :0 x1 b :0 x6 c:0 xb d:0 xa s:0 x10 i :0 xcc f:0 x6[I] op:0 x1 arg1:0 x8 arg2:0 x1[s] SYS 0 x8 d[s] ... write[s] ... return value (in register d): 0 xb[V] a :0 x1 b :0 x6 c:0 xb d:0 xb s:0 x10 i :0 xcd f:0 x6[I] op:0 x20 arg1:0 x4 arg2:0 x1[s] IMM a = 0 x1[V] a :0 x1 b :0 x6 c:0 xb d:0 xb s:0 x10 i :0 xce f:0 x6[I] op:0 x1 arg1:0 x20 arg2:0 [s] SYS 0 x20 NONE[s] ... exit
还挺复杂的…下面的是idapro的逆向源码:
1 2 3 4 5 6 7 8 9 10 11 12 13 void __fastcall __noreturn interpreter_loop (__int64 a1) unsigned __int8 v1; while ( 1 )1029 );1029 ) = v1 + 1 ;unsigned __int16 *)(a1 + 3LL * v1) | ((unsigned __int64)*(unsigned __int8 *)(a1 + 3LL * v1 + 2 ) << 16 ));
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 __int64 __fastcall interpret_instruction (unsigned __int8 *a1, __int64 a2) printf ("[V] a:%#hhx b:%#hhx c:%#hhx d:%#hhx s:%#hhx i:%#hhx f:%#hhx\n" ,1024 ],1025 ],1026 ],1027 ],1028 ],1029 ],1030 ]);printf ("[I] op:%#hhx arg1:%#hhx arg2:%#hhx\n" , BYTE2(a2), (unsigned __int8)a2, BYTE1(a2));if ( (a2 & 0x200000 ) != 0 )if ( (a2 & 0x100000 ) != 0 )if ( (a2 & 0x40000 ) != 0 )if ( (a2 & 0x80000 ) != 0 )if ( (a2 & 0x20000 ) != 0 )if ( (a2 & 0x800000 ) != 0 )if ( (a2 & 0x400000 ) != 0 )1 ;if ( (a2 & 0x10000 ) != 0 )return interpret_sys(a1, a2);return result;
看一下新操作STK所做的操作:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 __int64 __fastcall interpret_stk (__int64 a1, __int16 a2) const char *v2; const char *v3; const char *v4; unsigned __int8 v5; const char *v7; unsigned __int8 memory; const char *)describe_register(HIBYTE(a2));const char *)describe_register((unsigned __int8)a2);printf ("[s] STK %s %s\n" , v3, v2);if ( HIBYTE(a2) )const char *)describe_register(HIBYTE(a2));printf ("[s] ... pushing %s\n" , v4);1028 );unsigned __int8 *)(a1 + 1028 ), v5);unsigned __int8)a2;if ( (_BYTE)a2 )const char *)describe_register((unsigned __int8)a2);printf ("[s] ... popping %s\n" , v7);unsigned __int8 *)(a1 + 1028 ));unsigned __int8)a2, memory);1028 );return result;
可以看出,这是模拟栈,并且把栈地址设置为a1[1028]
最后做出来,感觉不太需要关心这个栈,其实只需要看CMP指令,然后发现它第一个比较的数是a1[0x3b]和a1[0xa9],第二个比较的数是a1[3a]和a1[a8]。一个逆序比较,那么不用管,只需要调整一下顺序就可以了。把前俩放到最后就行了。
level19.1 我们通过gdb脚本,然后拿到对应的opcode以及arg1和arg2。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 b *0 x589192137cd1set $fd = fopen("/home/hacker/Desktop/rsi.txt" ,"w" )while 1set $rsi_value = $rsi set $a = *(unsigned char*)($rax + 0x400)set $b = *(unsigned char*)($rax + 0x401)set $c = *(unsigned char*)($rax + 0x402)set $d = *(unsigned char*)($rax + 0x403)set $s = *(unsigned char*)($rax + 0x404)set $i = *(unsigned char*)($rax + 0x405)set $f = *(unsigned char*)($rax + 0x406)$fd ,"a:%x b:%x c:%x d:%x s:%x i:%x f:%x\n" , $a ,$b ,$c ,$d ,$s ,$i ,$f )$fd , "0x%lx\n" , $rsi_value )$fd )
这个break的地址是通过gdb调试过程中拿到的,其实就是死循环中调用的那个函数的call指令的地址。然后,$rax在这时存储的是a1的首地址,然后我们发现偏移地址就是+0x403,这可以通过调试或者19.0这个level拿到。然后,就打印出来a,b,c,d,s,i,f变量的值。以此来判断,我们要发送的字符串,以及其做的代码混淆处理。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 220 221 222 223 224 225 226 227 228 229 230 231 232 233 234 235 236 237 238 239 240 241 242 243 244 245 246 247 248 249 250 251 252 253 254 255 256 257 258 259 260 261 262 263 264 265 266 a :0 b:0 c:0 d:0 s:0 i:1 f:0 0x20402 a :0 b:0 c:0 d:2 s:0 i:2 f:0 0x801004 a :0 b:0 c:0 d:2 s:0 i:3 f:0 0x204c2 a :0 b:0 c:0 d:c2 s:0 i:4 f:0 0x2206c a :0 b:0 c:6 c d:c2 s:0 i:5 f:0 0x402004 a :0 b:0 c:6 c d:c2 s:0 i:6 f:0 0x2044d a :0 b:0 c:6 c d:4 d s:0 i:7 f:0 0x2206d a :0 b:0 c:6 d d:4 d s:0 i:8 f:0 0x402004 a :0 b:0 c:6 d d:4 d s:0 i:9 f:0 0x20442 a :0 b:0 c:6 d d:42 s:0 i:a f:0 0x2206e a :0 b:0 c:6 e d:42 s:0 i:b f:0 0x402004 a :0 b:0 c:6 e d:42 s:0 i:c f:0 0x20482 a :0 b:0 c:6 e d:82 s:0 i:d f:0 0x2206f a :0 b:0 c:6 f d:82 s:0 i:e f:0 0x402004 a :0 b:0 c:6 f d:82 s:0 i:f f:0 0x2042d a :0 b:0 c:6 f d:2 d s:0 i:10 f:0 0x22070 a :0 b:0 c:70 d:2 d s:0 i:11 f:0 0x402004 a :0 b:0 c:70 d:2 d s:0 i:12 f:0 0x204e5 a :0 b:0 c:70 d:e5 s:0 i:13 f:0 0x22071 a :0 b:0 c:71 d:e5 s:0 i:14 f:0 0x402004 a :0 b:0 c:71 d:e5 s:0 i:15 f:0 0x20464 a :0 b:0 c:71 d:64 s:0 i:16 f:0 0x22072 a :0 b:0 c:72 d:64 s:0 i:17 f:0 0x402004 a :0 b:0 c:72 d:64 s:0 i:18 f:0 0x20498 a :0 b:0 c:72 d:98 s:0 i:19 f:0 0x22073 a :0 b:0 c:73 d:98 s:0 i:1 a f:0 0x402004 a :0 b:0 c:73 d:98 s:0 i:1 b f:0 0x204f7 a :0 b:0 c:73 d:f7 s:0 i:1 c f:0 0x22074 a :0 b:0 c:74 d:f7 s:0 i:1 d f:0 0x402004 a :0 b:0 c:74 d:f7 s:0 i:1 e f:0 0x204ac a :0 b:0 c:74 d:ac s:0 i:1 f f:0 0x22075 a :0 b:0 c:75 d:ac s:0 i:20 f:0 0x402004 a :0 b:0 c:75 d:ac s:0 i:21 f:0 0x20465 a :0 b:0 c:75 d:65 s:0 i:22 f:0 0x22076 a :0 b:0 c:76 d:65 s:0 i:23 f:0 0x402004 a :0 b:0 c:76 d:65 s:0 i:24 f:0 0x21024 a :0 b:0 c:76 d:65 s:0 i:25 f:0 0x800002 a :0 b:0 c:76 d:65 s:1 i:26 f:0 0x800040 a :0 b:0 c:76 d:65 s:2 i:27 f:0 0x800020 a :0 b:0 c:76 d:65 s:3 i:28 f:0 0x24001 a :0 b:1 c:76 d:65 s:3 i:29 f:0 0x14008 a :0 b:4 c:76 d:65 s:3 i:2 a f:0 0x2044b a :0 b:4 c:76 d:4 b s:3 i:2 b f:0 0x800004 a :0 b:4 c:76 d:4 b s:4 i:2 c f:0 0x20445 a :0 b:4 c:76 d:45 s:4 i:2 d f:0 0x800004 a :0 b:4 c:76 d:45 s:5 i:2 e f:0 0x20459 a :0 b:4 c:76 d:59 s:5 i:2 f f:0 0x800004 a :0 b:4 c:76 d:59 s:6 i:30 f:0 0x2043a a :0 b:4 c:76 d:3 a s:6 i:31 f:0 0x800004 a :0 b:4 c:76 d:3 a s:7 i:32 f:0 0x20420 a :0 b:4 c:76 d:20 s:7 i:33 f:0 0x800004 a :0 b:4 c:76 d:20 s:8 i:34 f:0 0x22005 a :0 b:4 c:5 d:20 s:8 i:35 f:0 0x20201 a :1 b:4 c:5 d:20 s:8 i:36 f:0 0x100104 a :1 b:4 c:5 d:5 s:8 i:37 f:0 0x802000 a :1 b:4 c:20 d:5 s:7 i:38 f:0 0x804000 a :1 b:3 a c:20 d:5 s:6 i:39 f:0 0x800200 a :59 b:3 a c:20 d:5 s:5 i:3 a f:0 0x800002 a :59 b:3 a c:20 d:5 s:6 i:3 b f:0 0x800040 a :59 b:3 a c:20 d:5 s:7 i:3 c f:0 0x800020 a :59 b:3 a c:20 d:5 s:8 i:3 d f:0 0x24030 a :59 b:30 c:20 d:5 s:8 i:3 e f:0 0x2200b a :59 b:30 c:b d:5 s:8 i:3 f f:0 0x20200 a :0 b:30 c:b d:5 s:8 i:40 f:0 0x100404 a :0 b:30 c:b d:b s:8 i:41 f:0 0x802000 a :0 b:30 c:20 d:b s:7 i:42 f:0 0x804000 a :0 b:3 a c:20 d:b s:6 i:43 f:0 0x800200 a :59 b:3 a c:20 d:b s:5 i:44 f:0 0x21044 a :59 b:3 a c:20 d:b s:5 i:45 f:0 0x800002 a :59 b:3 a c:20 d:b s:6 i:46 f:0 0x800040 a :59 b:3 a c:20 d:b s:7 i:47 f:0 0x800020 a :59 b:3 a c:20 d:b s:8 i:48 f:0 0x802000 a :59 b:3 a c:20 d:b s:7 i:49 f:0 0x804000 a :59 b:3 a c:20 d:b s:6 i:4 a f:0 0x800200 a :59 b:3 a c:20 d:b s:5 i:4 b f:0 0x210ce a :59 b:3 a c:20 d:b s:5 i:cf f:0 0x20230 a :30 b:3 a c:20 d:b s:5 i:d0 f:0 0x2406e a :30 b:6 e c:20 d:b s:5 i:d1 f:0 0x22009 a :30 b:6 e c:9 d:b s:5 i:d2 f:0 0x20402 a :30 b:6 e c:9 d:2 s:5 i:d3 f:0 0x10410 a :30 b:6 e c:9 d:d5 s:5 i:d4 f:0 0x800004 a :30 b:6 e c:9 d:d5 s:6 i:d5 f:0 0x2109b a :30 b:6 e c:9 d:d5 s:6 i:9 c f:0 0x10220 a :39 b:6 e c:9 d:d5 s:6 i:9 d f:0 0x14020 a :39 b:77 c:9 d:d5 s:6 i:9 e f:0 0x204ff a :39 b:77 c:9 d:ff s:6 i:9 f f:0 0x10204 a :38 b:77 c:9 d:ff s:6 i:a0 f:0 0x14004 a :38 b:76 c:9 d:ff s:6 i:a1 f:0 0x800002 a :38 b:76 c:9 d:ff s:7 i:a2 f:0 0x800040 a :38 b:76 c:9 d:ff s:8 i:a3 f:0 0x80202 a :64 b:76 c:9 d:ff s:8 i:a4 f:0 0x84040 a :64 b:65 c:9 d:ff s:8 i:a5 f:0 0x200240 # cmp a :64 b:65 c:9 d:ff s:8 i:a6 f:9 0x804000 a :64 b:76 c:9 d:ff s:7 i:a7 f:9 0x800200 a :38 b:76 c:9 d:ff s:6 i:a8 f:9 0x204af a :38 b:76 c:9 d:af s:6 i:a9 f:9 0x40804 a :38 b:76 c:9 d:af s:6 i:b0 f:9 0x800420 a :38 b:76 c:9 d:9 s:6 i:b1 f:9 0x801000 a :38 b:76 c:9 d:9 s:5 i:d6 f:9 0x22000 a :38 b:76 c:0 d:9 s:5 i:d7 f:9 0x200420 # cmpa :38 b:76 c:0 d:9 s:5 i:d8 f:18 0x2044b a :38 b:76 c:0 d:4 b s:5 i:d9 f:18 0x40404 a :38 b:76 c:0 d:4 b s:5 i:da f:18 0x204b1 a :38 b:76 c:0 d:b1 s:5 i:db f:18 0x41104 a :38 b:76 c:0 d:b1 s:5 i:b2 f:18 0x24001 a :38 b:1 c:0 d:b1 s:5 i:b3 f:18 0x14008 a :38 b:6 c:0 d:b1 s:5 i:b4 f:18 0x20449 a :38 b:6 c:0 d:49 s:5 i:b5 f:18 0x800004 a :38 b:6 c:0 d:49 s:6 i:b6 f:18 0x2044e a :38 b:6 c:0 d:4 e s:6 i:b7 f:18 0x800004 a :38 b:6 c:0 d:4 e s:7 i:b8 f:18 0x20443 a :38 b:6 c:0 d:43 s:7 i:b9 f:18 0x800004 a :38 b:6 c:0 d:43 s:8 i:ba f:18 0x2044f a :38 b:6 c:0 d:4 f s:8 i:bb f:18 0x800004 a :38 b:6 c:0 d:4 f s:9 i:bc f:18 0x20452 a :38 b:6 c:0 d:52 s:9 i:bd f:18 0x800004 a :38 b:6 c:0 d:52 s:a i:be f:18 0x20452 a :38 b:6 c:0 d:52 s:a i:bf f:18 0x800004 a :38 b:6 c:0 d:52 s:b i:c0 f:18 0x20445 a :38 b:6 c:0 d:45 s:b i:c1 f:18 0x800004 a :38 b:6 c:0 d:45 s:c i:c2 f:18 0x20443 a :38 b:6 c:0 d:43 s:c i:c3 f:18 0x800004 a :38 b:6 c:0 d:43 s:d i:c4 f:18 0x20454 a :38 b:6 c:0 d:54 s:d i:c5 f:18 0x800004 a :38 b:6 c:0 d:54 s:e i:c6 f:18 0x20421 a :38 b:6 c:0 d:21 s:e i:c7 f:18 0x800004 a :38 b:6 c:0 d:21 s:f i:c8 f:18 0x2040a a :38 b:6 c:0 d:a s:f i:c9 f:18 0x800004 a :38 b:6 c:0 d:a s:10 i:ca f:18 0x2200b a :38 b:6 c:b d:a s:10 i:cb f:18 0x20201 a :1 b:6 c:b d:a s:10 i:cc f:18 0x100104 a :1 b:6 c:b d:b s:10 i:cd f:18 0x20201 a :1 b:6 c:b d:b s:10 i:ce f:18 0x100200
具体的opcode对应的操作指令,可以通过19.0对应出来。那么最后,分析发现用户输入偏移为0x30,目标字符串的偏移为0x6c。然后cmp指令比较时,从0x38偏移处开始比较的,然后目标字符串从0x76开始比较的。最后做相应处理即可。exp如下:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 from pwn import *"/challenge/babyrev-level-19-1" )0x42 , 0x82 , 0x2d , 0xe5 , 0x64 , 0x98 , 0xf7 , 0xac , 0x65 ,0xc2 , 0x4d ]b'' '11B' , *al)while (z):print (z)
level20.0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 [V] a :0 b :0 c:0 d:0 s:0 i :0 x1 f:0 [I] op:0 x20 arg1:0 x40 arg2:0 x1e[s] IMM b = 0 x1e[V] a :0 b :0 x1e c:0 d:0 s:0 i :0 x2 f:0 [I] op:0 x80 arg1:0 x4 arg2:0 x40[s] STK i b [s] ... pushing b [s] ... popping i [V] a :0 b :0 x1e c:0 d:0 s:0 i :0 x1f f:0 [I] op:0 x20 arg1:0 x40 arg2:0 xde[s] IMM b = 0 xde[V] a :0 b :0 xde c:0 d:0 s:0 i :0 x20 f:0 [I] op:0 x20 arg1:0 x20 arg2:0 x5[s] IMM c = 0 x5[V] a :0 b :0 xde c:0 x5 d:0 s:0 i :0 x21 f:0 [I] op:0 x20 arg1:0 x2 arg2:0 x1[s] IMM a = 0 x1[V] a :0 x1 b :0 xde c:0 x5 d:0 s:0 i :0 x22 f:0 [I] op:0 x2 arg1:0 x2 arg2:0 x1[s] SYS 0 x2 d[s] ... write[s] ... return value (in register d): 0 x5[V] a :0 x1 b :0 xde c:0 x5 d:0 x5 s:0 i :0 x23 f:0 [I] op:0 x80 arg1:0 arg2:0 x2[s] STK NONE a [s] ... pushing a [V] a :0 x1 b :0 xde c:0 x5 d:0 x5 s:0 x1 i :0 x24 f:0 [I] op:0 x80 arg1:0 arg2:0 x40[s] STK NONE b [s] ... pushing b [V] a :0 x1 b :0 xde c:0 x5 d:0 x5 s:0 x2 i :0 x25 f:0 [I] op:0 x80 arg1:0 arg2:0 x20[s] STK NONE c[s] ... pushing c[V] a :0 x1 b :0 xde c:0 x5 d:0 x5 s:0 x3 i :0 x26 f:0 [I] op:0 x20 arg1:0 x40 arg2:0 x30[s] IMM b = 0 x30[V] a :0 x1 b :0 x30 c:0 x5 d:0 x5 s:0 x3 i :0 x27 f:0 [I] op:0 x20 arg1:0 x20 arg2:0 x1b[s] IMM c = 0 x1b[V] a :0 x1 b :0 x30 c:0 x1b d:0 x5 s:0 x3 i :0 x28 f:0 [I] op:0 x20 arg1:0 x2 arg2:0 [s] IMM a = 0 [V] a :0 b :0 x30 c:0 x1b d:0 x5 s:0 x3 i :0 x29 f:0 [I] op:0 x2 arg1:0 x1 arg2:0 x1[s] SYS 0 x1 d[s] ... read_memory123
输入后
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 220 221 222 223 224 225 226 227 228 229 230 231 232 233 234 235 236 237 238 239 240 241 242 243 244 245 246 247 248 249 250 251 252 253 254 255 256 257 258 259 260 261 262 263 264 265 266 267 268 269 270 271 272 273 274 275 276 277 278 279 280 281 282 283 284 285 286 287 288 289 290 291 292 293 294 295 296 297 298 299 300 301 302 303 304 305 306 307 308 309 310 311 312 313 314 315 316 317 318 319 320 321 322 323 324 325 326 327 328 329 330 331 332 333 334 335 336 337 338 339 340 341 342 343 344 345 346 347 348 349 350 351 352 353 354 355 356 357 358 359 360 361 362 363 364 365 366 367 368 369 370 371 372 373 374 375 376 377 378 379 380 381 382 383 384 385 386 387 388 389 390 391 392 393 394 395 396 397 398 399 400 401 402 403 404 405 406 407 408 409 410 411 412 413 414 415 416 417 418 419 420 421 422 423 424 425 426 427 428 429 430 431 432 433 434 435 436 437 438 439 440 441 442 443 444 445 446 447 448 449 450 451 452 453 454 455 456 457 458 459 460 461 462 463 464 465 466 467 468 469 [s ] ... return value (in register d): 0x4 V ] a:0 b:0x30 c:0x1b d:0x4 s:0x3 i:0x2a f:0 I ] op:0x80 arg1:0x20 arg2:0 s ] STK c NONEs ] ... popping cV ] a:0 b:0x30 c:0x5 d:0x4 s:0x2 i:0x2b f:0 I ] op:0x80 arg1:0x40 arg2:0 s ] STK b NONEs ] ... popping bV ] a:0 b:0xde c:0x5 d:0x4 s:0x1 i:0x2c f:0 I ] op:0x80 arg1:0x2 arg2:0 s ] STK a NONEs ] ... popping aV ] a:0x1 b:0xde c:0x5 d:0x4 s:0 i:0x2d f:0 I ] op:0x20 arg1:0x4 arg2:0x2d s ] IMM i = 0x2d V ] a:0x1 b:0xde c:0x5 d:0x4 s:0 i:0x2e f:0 I ] op:0x80 arg1:0 arg2:0x2 s ] STK NONE as ] ... pushing aV ] a:0x1 b:0xde c:0x5 d:0x4 s:0x1 i:0x2f f:0 I ] op:0x80 arg1:0 arg2:0x40 s ] STK NONE bs ] ... pushing bV ] a:0x1 b:0xde c:0x5 d:0x4 s:0x2 i:0x30 f:0 I ] op:0x80 arg1:0 arg2:0x20 s ] STK NONE cs ] ... pushing cV ] a:0x1 b:0xde c:0x5 d:0x4 s:0x3 i:0x31 f:0 I ] op:0x20 arg1:0x2 arg2:0x30 s ] IMM a = 0x30 V ] a:0x30 b:0xde c:0x5 d:0x4 s:0x3 i:0x32 f:0 I ] op:0x20 arg1:0x20 arg2:0xa5 s ] IMM c = 0xa5 V ] a:0x30 b:0xde c:0xa5 d:0x4 s:0x3 i:0x33 f:0 I ] op:0x40 arg1:0x40 arg2:0x2 s ] LDM b = *a # a1[0x30] = 0x31 V ] a:0x30 b:0x31 c:0xa5 d:0x4 s:0x3 i:0x34 f:0 I ] op:0x4 arg1:0x40 arg2:0x20 s ] ADD b c V ] a:0x30 b:0xd6 c:0xa5 d:0x4 s:0x3 i:0x35 f:0 I ] op:0x1 arg1:0x2 arg2:0x40 s ] STM *a = b # a1[0x30] = 0x31 + 0xa5 V ] a:0x30 b:0xd6 c:0xa5 d:0x4 s:0x3 i:0x36 f:0 I ] op:0x20 arg1:0x2 arg2:0x31 s ] IMM a = 0x31 V ] a:0x31 b:0xd6 c:0xa5 d:0x4 s:0x3 i:0x37 f:0 I ] op:0x20 arg1:0x20 arg2:0xce s ] IMM c = 0xce V ] a:0x31 b:0xd6 c:0xce d:0x4 s:0x3 i:0x38 f:0 I ] op:0x40 arg1:0x40 arg2:0x2 s ] LDM b = *a # a1[0x31] = 0x32 V ] a:0x31 b:0x32 c:0xce d:0x4 s:0x3 i:0x39 f:0 I ] op:0x4 arg1:0x40 arg2:0x20 s ] ADD b cV ] a:0x31 b:0 c:0xce d:0x4 s:0x3 i:0x3a f:0 I ] op:0x1 arg1:0x2 arg2:0x40 s ] STM *a = b # a1[0x31] = 0x32 + 0xce V ] a:0x31 b:0 c:0xce d:0x4 s:0x3 i:0x3b f:0 I ] op:0x20 arg1:0x2 arg2:0x32 s ] IMM a = 0x32 V ] a:0x32 b:0 c:0xce d:0x4 s:0x3 i:0x3c f:0 I ] op:0x20 arg1:0x20 arg2:0x67 s ] IMM c = 0x67 V ] a:0x32 b:0 c:0x67 d:0x4 s:0x3 i:0x3d f:0 I ] op:0x40 arg1:0x40 arg2:0x2 s ] LDM b = *aV ] a:0x32 b:0x33 c:0x67 d:0x4 s:0x3 i:0x3e f:0 I ] op:0x4 arg1:0x40 arg2:0x20 s ] ADD b c # a1[0x32] = 0x33 + 0x67 V ] a:0x32 b:0x9a c:0x67 d:0x4 s:0x3 i:0x3f f:0 I ] op:0x1 arg1:0x2 arg2:0x40 s ] STM *a = bV ] a:0x32 b:0x9a c:0x67 d:0x4 s:0x3 i:0x40 f:0 I ] op:0x20 arg1:0x2 arg2:0x33 s ] IMM a = 0x33 V ] a:0x33 b:0x9a c:0x67 d:0x4 s:0x3 i:0x41 f:0 I ] op:0x20 arg1:0x20 arg2:0xab s ] IMM c = 0xab V ] a:0x33 b:0x9a c:0xab d:0x4 s:0x3 i:0x42 f:0 I ] op:0x40 arg1:0x40 arg2:0x2 s ] LDM b = *aV ] a:0x33 b:0xa c:0xab d:0x4 s:0x3 i:0x43 f:0 I ] op:0x4 arg1:0x40 arg2:0x20 s ] ADD b cV ] a:0x33 b:0xb5 c:0xab d:0x4 s:0x3 i:0x44 f:0 I ] op:0x1 arg1:0x2 arg2:0x40 s ] STM *a = b # a1[0x33] = 0xa + 0xab V ] a:0x33 b:0xb5 c:0xab d:0x4 s:0x3 i:0x45 f:0 I ] op:0x20 arg1:0x2 arg2:0x34 s ] IMM a = 0x34 V ] a:0x34 b:0xb5 c:0xab d:0x4 s:0x3 i:0x46 f:0 I ] op:0x20 arg1:0x20 arg2:0x98 s ] IMM c = 0x98 V ] a:0x34 b:0xb5 c:0x98 d:0x4 s:0x3 i:0x47 f:0 I ] op:0x40 arg1:0x40 arg2:0x2 s ] LDM b = *aV ] a:0x34 b:0 c:0x98 d:0x4 s:0x3 i:0x48 f:0 I ] op:0x4 arg1:0x40 arg2:0x20 s ] ADD b cV ] a:0x34 b:0x98 c:0x98 d:0x4 s:0x3 i:0x49 f:0 I ] op:0x1 arg1:0x2 arg2:0x40 s ] STM *a = bV ] a:0x34 b:0x98 c:0x98 d:0x4 s:0x3 i:0x4a f:0 I ] op:0x20 arg1:0x2 arg2:0x35 s ] IMM a = 0x35 V ] a:0x35 b:0x98 c:0x98 d:0x4 s:0x3 i:0x4b f:0 I ] op:0x20 arg1:0x20 arg2:0x46 s ] IMM c = 0x46 V ] a:0x35 b:0x98 c:0x46 d:0x4 s:0x3 i:0x4c f:0 I ] op:0x40 arg1:0x40 arg2:0x2 s ] LDM b = *aV ] a:0x35 b:0 c:0x46 d:0x4 s:0x3 i:0x4d f:0 I ] op:0x4 arg1:0x40 arg2:0x20 s ] ADD b cV ] a:0x35 b:0x46 c:0x46 d:0x4 s:0x3 i:0x4e f:0 I ] op:0x1 arg1:0x2 arg2:0x40 s ] STM *a = bV ] a:0x35 b:0x46 c:0x46 d:0x4 s:0x3 i:0x4f f:0 I ] op:0x20 arg1:0x2 arg2:0x36 s ] IMM a = 0x36 V ] a:0x36 b:0x46 c:0x46 d:0x4 s:0x3 i:0x50 f:0 I ] op:0x20 arg1:0x20 arg2:0x63 s ] IMM c = 0x63 V ] a:0x36 b:0x46 c:0x63 d:0x4 s:0x3 i:0x51 f:0 I ] op:0x40 arg1:0x40 arg2:0x2 s ] LDM b = *aV ] a:0x36 b:0 c:0x63 d:0x4 s:0x3 i:0x52 f:0 I ] op:0x4 arg1:0x40 arg2:0x20 s ] ADD b cV ] a:0x36 b:0x63 c:0x63 d:0x4 s:0x3 i:0x53 f:0 I ] op:0x1 arg1:0x2 arg2:0x40 s ] STM *a = bV ] a:0x36 b:0x63 c:0x63 d:0x4 s:0x3 i:0x54 f:0 I ] op:0x20 arg1:0x2 arg2:0x37 s ] IMM a = 0x37 V ] a:0x37 b:0x63 c:0x63 d:0x4 s:0x3 i:0x55 f:0 I ] op:0x20 arg1:0x20 arg2:0xe1 s ] IMM c = 0xe1 V ] a:0x37 b:0x63 c:0xe1 d:0x4 s:0x3 i:0x56 f:0 I ] op:0x40 arg1:0x40 arg2:0x2 s ] LDM b = *aV ] a:0x37 b:0 c:0xe1 d:0x4 s:0x3 i:0x57 f:0 I ] op:0x4 arg1:0x40 arg2:0x20 s ] ADD b cV ] a:0x37 b:0xe1 c:0xe1 d:0x4 s:0x3 i:0x58 f:0 I ] op:0x1 arg1:0x2 arg2:0x40 s ] STM *a = bV ] a:0x37 b:0xe1 c:0xe1 d:0x4 s:0x3 i:0x59 f:0 I ] op:0x20 arg1:0x2 arg2:0x38 s ] IMM a = 0x38 V ] a:0x38 b:0xe1 c:0xe1 d:0x4 s:0x3 i:0x5a f:0 I ] op:0x20 arg1:0x20 arg2:0x48 s ] IMM c = 0x48 V ] a:0x38 b:0xe1 c:0x48 d:0x4 s:0x3 i:0x5b f:0 I ] op:0x40 arg1:0x40 arg2:0x2 s ] LDM b = *aV ] a:0x38 b:0 c:0x48 d:0x4 s:0x3 i:0x5c f:0 I ] op:0x4 arg1:0x40 arg2:0x20 s ] ADD b cV ] a:0x38 b:0x48 c:0x48 d:0x4 s:0x3 i:0x5d f:0 I ] op:0x1 arg1:0x2 arg2:0x40 s ] STM *a = bV ] a:0x38 b:0x48 c:0x48 d:0x4 s:0x3 i:0x5e f:0 I ] op:0x20 arg1:0x2 arg2:0x39 s ] IMM a = 0x39 V ] a:0x39 b:0x48 c:0x48 d:0x4 s:0x3 i:0x5f f:0 I ] op:0x20 arg1:0x20 arg2:0x37 s ] IMM c = 0x37 V ] a:0x39 b:0x48 c:0x37 d:0x4 s:0x3 i:0x60 f:0 I ] op:0x40 arg1:0x40 arg2:0x2 s ] LDM b = *aV ] a:0x39 b:0 c:0x37 d:0x4 s:0x3 i:0x61 f:0 I ] op:0x4 arg1:0x40 arg2:0x20 s ] ADD b cV ] a:0x39 b:0x37 c:0x37 d:0x4 s:0x3 i:0x62 f:0 I ] op:0x1 arg1:0x2 arg2:0x40 s ] STM *a = bV ] a:0x39 b:0x37 c:0x37 d:0x4 s:0x3 i:0x63 f:0 I ] op:0x20 arg1:0x2 arg2:0x3a s ] IMM a = 0x3a V ] a:0x3a b:0x37 c:0x37 d:0x4 s:0x3 i:0x64 f:0 I ] op:0x20 arg1:0x20 arg2:0x3e s ] IMM c = 0x3e V ] a:0x3a b:0x37 c:0x3e d:0x4 s:0x3 i:0x65 f:0 I ] op:0x40 arg1:0x40 arg2:0x2 s ] LDM b = *aV ] a:0x3a b:0 c:0x3e d:0x4 s:0x3 i:0x66 f:0 I ] op:0x4 arg1:0x40 arg2:0x20 s ] ADD b cV ] a:0x3a b:0x3e c:0x3e d:0x4 s:0x3 i:0x67 f:0 I ] op:0x1 arg1:0x2 arg2:0x40 s ] STM *a = bV ] a:0x3a b:0x3e c:0x3e d:0x4 s:0x3 i:0x68 f:0 I ] op:0x20 arg1:0x2 arg2:0x3b s ] IMM a = 0x3b V ] a:0x3b b:0x3e c:0x3e d:0x4 s:0x3 i:0x69 f:0 I ] op:0x20 arg1:0x20 arg2:0x7f s ] IMM c = 0x7f V ] a:0x3b b:0x3e c:0x7f d:0x4 s:0x3 i:0x6a f:0 I ] op:0x40 arg1:0x40 arg2:0x2 s ] LDM b = *aV ] a:0x3b b:0 c:0x7f d:0x4 s:0x3 i:0x6b f:0 I ] op:0x4 arg1:0x40 arg2:0x20 s ] ADD b cV ] a:0x3b b:0x7f c:0x7f d:0x4 s:0x3 i:0x6c f:0 I ] op:0x1 arg1:0x2 arg2:0x40 s ] STM *a = bV ] a:0x3b b:0x7f c:0x7f d:0x4 s:0x3 i:0x6d f:0 I ] op:0x20 arg1:0x2 arg2:0x3c s ] IMM a = 0x3c V ] a:0x3c b:0x7f c:0x7f d:0x4 s:0x3 i:0x6e f:0 I ] op:0x20 arg1:0x20 arg2:0xc1 s ] IMM c = 0xc1 V ] a:0x3c b:0x7f c:0xc1 d:0x4 s:0x3 i:0x6f f:0 I ] op:0x40 arg1:0x40 arg2:0x2 s ] LDM b = *aV ] a:0x3c b:0 c:0xc1 d:0x4 s:0x3 i:0x70 f:0 I ] op:0x4 arg1:0x40 arg2:0x20 s ] ADD b cV ] a:0x3c b:0xc1 c:0xc1 d:0x4 s:0x3 i:0x71 f:0 I ] op:0x1 arg1:0x2 arg2:0x40 s ] STM *a = bV ] a:0x3c b:0xc1 c:0xc1 d:0x4 s:0x3 i:0x72 f:0 I ] op:0x20 arg1:0x2 arg2:0x3d s ] IMM a = 0x3d V ] a:0x3d b:0xc1 c:0xc1 d:0x4 s:0x3 i:0x73 f:0 I ] op:0x20 arg1:0x20 arg2:0xfa s ] IMM c = 0xfa V ] a:0x3d b:0xc1 c:0xfa d:0x4 s:0x3 i:0x74 f:0 I ] op:0x40 arg1:0x40 arg2:0x2 s ] LDM b = *aV ] a:0x3d b:0 c:0xfa d:0x4 s:0x3 i:0x75 f:0 I ] op:0x4 arg1:0x40 arg2:0x20 s ] ADD b cV ] a:0x3d b:0xfa c:0xfa d:0x4 s:0x3 i:0x76 f:0 I ] op:0x1 arg1:0x2 arg2:0x40 s ] STM *a = bV ] a:0x3d b:0xfa c:0xfa d:0x4 s:0x3 i:0x77 f:0 I ] op:0x20 arg1:0x2 arg2:0x3e s ] IMM a = 0x3e V ] a:0x3e b:0xfa c:0xfa d:0x4 s:0x3 i:0x78 f:0 I ] op:0x20 arg1:0x20 arg2:0x53 s ] IMM c = 0x53 V ] a:0x3e b:0xfa c:0x53 d:0x4 s:0x3 i:0x79 f:0 I ] op:0x40 arg1:0x40 arg2:0x2 s ] LDM b = *aV ] a:0x3e b:0 c:0x53 d:0x4 s:0x3 i:0x7a f:0 I ] op:0x4 arg1:0x40 arg2:0x20 s ] ADD b cV ] a:0x3e b:0x53 c:0x53 d:0x4 s:0x3 i:0x7b f:0 I ] op:0x1 arg1:0x2 arg2:0x40 s ] STM *a = bV ] a:0x3e b:0x53 c:0x53 d:0x4 s:0x3 i:0x7c f:0 I ] op:0x20 arg1:0x2 arg2:0x3f s ] IMM a = 0x3f V ] a:0x3f b:0x53 c:0x53 d:0x4 s:0x3 i:0x7d f:0 I ] op:0x20 arg1:0x20 arg2:0x5f s ] IMM c = 0x5f V ] a:0x3f b:0x53 c:0x5f d:0x4 s:0x3 i:0x7e f:0 I ] op:0x40 arg1:0x40 arg2:0x2 s ] LDM b = *aV ] a:0x3f b:0 c:0x5f d:0x4 s:0x3 i:0x7f f:0 I ] op:0x4 arg1:0x40 arg2:0x20 s ] ADD b cV ] a:0x3f b:0x5f c:0x5f d:0x4 s:0x3 i:0x80 f:0 I ] op:0x1 arg1:0x2 arg2:0x40 s ] STM *a = bV ] a:0x3f b:0x5f c:0x5f d:0x4 s:0x3 i:0x81 f:0 I ] op:0x20 arg1:0x2 arg2:0x40 s ] IMM a = 0x40 V ] a:0x40 b:0x5f c:0x5f d:0x4 s:0x3 i:0x82 f:0 I ] op:0x20 arg1:0x20 arg2:0x99 s ] IMM c = 0x99 V ] a:0x40 b:0x5f c:0x99 d:0x4 s:0x3 i:0x83 f:0 I ] op:0x40 arg1:0x40 arg2:0x2 s ] LDM b = *aV ] a:0x40 b:0 c:0x99 d:0x4 s:0x3 i:0x84 f:0 I ] op:0x4 arg1:0x40 arg2:0x20 s ] ADD b cV ] a:0x40 b:0x99 c:0x99 d:0x4 s:0x3 i:0x85 f:0 I ] op:0x1 arg1:0x2 arg2:0x40 s ] STM *a = bV ] a:0x40 b:0x99 c:0x99 d:0x4 s:0x3 i:0x86 f:0 I ] op:0x20 arg1:0x2 arg2:0x41 s ] IMM a = 0x41 V ] a:0x41 b:0x99 c:0x99 d:0x4 s:0x3 i:0x87 f:0 I ] op:0x20 arg1:0x20 arg2:0x31 s ] IMM c = 0x31 V ] a:0x41 b:0x99 c:0x31 d:0x4 s:0x3 i:0x88 f:0 I ] op:0x40 arg1:0x40 arg2:0x2 s ] LDM b = *aV ] a:0x41 b:0 c:0x31 d:0x4 s:0x3 i:0x89 f:0 I ] op:0x4 arg1:0x40 arg2:0x20 s ] ADD b cV ] a:0x41 b:0x31 c:0x31 d:0x4 s:0x3 i:0x8a f:0 I ] op:0x1 arg1:0x2 arg2:0x40 s ] STM *a = bV ] a:0x41 b:0x31 c:0x31 d:0x4 s:0x3 i:0x8b f:0 I ] op:0x20 arg1:0x2 arg2:0x42 s ] IMM a = 0x42 V ] a:0x42 b:0x31 c:0x31 d:0x4 s:0x3 i:0x8c f:0 I ] op:0x20 arg1:0x20 arg2:0x38 s ] IMM c = 0x38 V ] a:0x42 b:0x31 c:0x38 d:0x4 s:0x3 i:0x8d f:0 I ] op:0x40 arg1:0x40 arg2:0x2 s ] LDM b = *aV ] a:0x42 b:0 c:0x38 d:0x4 s:0x3 i:0x8e f:0 I ] op:0x4 arg1:0x40 arg2:0x20 s ] ADD b cV ] a:0x42 b:0x38 c:0x38 d:0x4 s:0x3 i:0x8f f:0 I ] op:0x1 arg1:0x2 arg2:0x40 s ] STM *a = bV ] a:0x42 b:0x38 c:0x38 d:0x4 s:0x3 i:0x90 f:0 I ] op:0x20 arg1:0x2 arg2:0x43 s ] IMM a = 0x43 V ] a:0x43 b:0x38 c:0x38 d:0x4 s:0x3 i:0x91 f:0 I ] op:0x20 arg1:0x20 arg2:0x8f s ] IMM c = 0x8f V ] a:0x43 b:0x38 c:0x8f d:0x4 s:0x3 i:0x92 f:0 I ] op:0x40 arg1:0x40 arg2:0x2 s ] LDM b = *aV ] a:0x43 b:0 c:0x8f d:0x4 s:0x3 i:0x93 f:0 I ] op:0x4 arg1:0x40 arg2:0x20 s ] ADD b cV ] a:0x43 b:0x8f c:0x8f d:0x4 s:0x3 i:0x94 f:0 I ] op:0x1 arg1:0x2 arg2:0x40 s ] STM *a = bV ] a:0x43 b:0x8f c:0x8f d:0x4 s:0x3 i:0x95 f:0 I ] op:0x20 arg1:0x2 arg2:0x44 s ] IMM a = 0x44 V ] a:0x44 b:0x8f c:0x8f d:0x4 s:0x3 i:0x96 f:0 I ] op:0x20 arg1:0x20 arg2:0x89 s ] IMM c = 0x89 V ] a:0x44 b:0x8f c:0x89 d:0x4 s:0x3 i:0x97 f:0 I ] op:0x40 arg1:0x40 arg2:0x2 s ] LDM b = *aV ] a:0x44 b:0 c:0x89 d:0x4 s:0x3 i:0x98 f:0 I ] op:0x4 arg1:0x40 arg2:0x20 s ] ADD b cV ] a:0x44 b:0x89 c:0x89 d:0x4 s:0x3 i:0x99 f:0 I ] op:0x1 arg1:0x2 arg2:0x40 s ] STM *a = bV ] a:0x44 b:0x89 c:0x89 d:0x4 s:0x3 i:0x9a f:0 I ] op:0x80 arg1:0x20 arg2:0 s ] STK c NONEs ] ... popping cV ] a:0x44 b:0x89 c:0x5 d:0x4 s:0x2 i:0x9b f:0 I ] op:0x80 arg1:0x40 arg2:0 s ] STK b NONEs ] ... popping bV ] a:0x44 b:0xde c:0x5 d:0x4 s:0x1 i:0x9c f:0 I ] op:0x80 arg1:0x2 arg2:0 s ] STK a NONEs ] ... popping aV ] a:0x1 b:0xde c:0x5 d:0x4 s:0 i:0x9d f:0 I ] op:0x20 arg1:0x4 arg2:0x9d s ] IMM i = 0x9d V ] a:0x1 b:0xde c:0x5 d:0x4 s:0 i:0x9e f:0 I ] op:0x20 arg1:0x2 arg2:0x30 s ] IMM a = 0x30 V ] a:0x30 b:0xde c:0x5 d:0x4 s:0 i:0x9f f:0 I ] op:0x20 arg1:0x40 arg2:0xa3 s ] IMM b = 0xa3 V ] a:0x30 b:0xa3 c:0x5 d:0x4 s:0 i:0xa0 f:0 I ] op:0x20 arg1:0x20 arg2:0x15 s ] IMM c = 0x15 V ] a:0x30 b:0xa3 c:0x15 d:0x4 s:0 i:0xa1 f:0 I ] op:0x20 arg1:0x1 arg2:0x2 s ] IMM d = 0x2 V ] a:0x30 b:0xa3 c:0x15 d:0x2 s:0 i:0xa2 f:0 I ] op:0x4 arg1:0x1 arg2:0x4 s ] ADD d iV ] a:0x30 b:0xa3 c:0x15 d:0xa4 s:0 i:0xa3 f:0 I ] op:0x80 arg1:0 arg2:0x1 s ] STK NONE ds ] ... pushing dV ] a:0x30 b:0xa3 c:0x15 d:0xa4 s:0x1 i:0xa4 f:0 I ] op:0x20 arg1:0x4 arg2:0x2 s ] IMM i = 0x2 V ] a:0x30 b:0xa3 c:0x15 d:0xa4 s:0x1 i:0x3 f:0 I ] op:0x4 arg1:0x2 arg2:0x20 s ] ADD a cV ] a:0x45 b:0xa3 c:0x15 d:0xa4 s:0x1 i:0x4 f:0 I ] op:0x4 arg1:0x40 arg2:0x20 s ] ADD b cV ] a:0x45 b:0xb8 c:0x15 d:0xa4 s:0x1 i:0x5 f:0 I ] op:0x20 arg1:0x1 arg2:0xff s ] IMM d = 0xff V ] a:0x45 b:0xb8 c:0x15 d:0xff s:0x1 i:0x6 f:0 I ] op:0x4 arg1:0x2 arg2:0x1 s ] ADD a dV ] a:0x44 b:0xb8 c:0x15 d:0xff s:0x1 i:0x7 f:0 I ] op:0x4 arg1:0x40 arg2:0x1 s ] ADD b dV ] a:0x44 b:0xb7 c:0x15 d:0xff s:0x1 i:0x8 f:0 I ] op:0x80 arg1:0 arg2:0x2 s ] STK NONE as ] ... pushing aV ] a:0x44 b:0xb7 c:0x15 d:0xff s:0x2 i:0x9 f:0 I ] op:0x80 arg1:0 arg2:0x40 s ] STK NONE bs ] ... pushing bV ] a:0x44 b:0xb7 c:0x15 d:0xff s:0x3 i:0xa f:0 ####### I ] op:0x40 arg1:0x2 arg2:0x2 s ] LDM a = *a # a1[0x44] V ] a:0x89 b:0xb7 c:0x15 d:0xff s:0x3 i:0xb f:0 I ] op:0x40 arg1:0x40 arg2:0x40 s ] LDM b = *b # a1[0xb7] V ] a:0x89 b:0x5b c:0x15 d:0xff s:0x3 i:0xc f:0 I ] op:0x8 arg1:0x2 arg2:0x40 s ] CMP a bV ] a:0x89 b:0x5b c:0x15 d:0xff s:0x3 i:0xd f:0x14 I ] op:0x80 arg1:0x40 arg2:0 s ] STK b NONEs ] ... popping bV ] a:0x89 b:0xb7 c:0x15 d:0xff s:0x2 i:0xe f:0x14 I ] op:0x80 arg1:0x2 arg2:0 s ] STK a NONEs ] ... popping aV ] a:0x44 b:0xb7 c:0x15 d:0xff s:0x1 i:0xf f:0x14 I ] op:0x20 arg1:0x1 arg2:0x16 s ] IMM d = 0x16 V ] a:0x44 b:0xb7 c:0x15 d:0x16 s:0x1 i:0x10 f:0x14 I ] op:0x10 arg1:0x4 arg2:0x1 j ] JMP N dj ] ... TAKENV ] a:0x44 b:0xb7 c:0x15 d:0x16 s:0x1 i:0x17 f:0x14 I ] op:0x80 arg1:0x1 arg2:0x20 s ] STK d cs ] ... pushing cs ] ... popping dV ] a:0x44 b:0xb7 c:0x15 d:0x15 s:0x1 i:0x18 f:0x14 I ] op:0x80 arg1:0x4 arg2:0 s ] STK i NONEs ] ... popping iV ] a:0x44 b:0xb7 c:0x15 d:0x15 s:0 i:0xa5 f:0x14 I ] op:0x20 arg1:0x20 arg2:0 s ] IMM c = 0 V ] a:0x44 b:0xb7 c:0 d:0x15 s:0 i:0xa6 f:0x14 I ] op:0x8 arg1:0x1 arg2:0x20 s ] CMP d cV ] a:0x44 b:0xb7 c:0 d:0x15 s:0 i:0xa7 f:0x14 I ] op:0x20 arg1:0x1 arg2:0xaa s ] IMM d = 0xaa V ] a:0x44 b:0xb7 c:0 d:0xaa s:0 i:0xa8 f:0x14 I ] op:0x10 arg1:0x1 arg2:0x1 j ] JMP E dj ] ... NOT TAKENV ] a:0x44 b:0xb7 c:0 d:0xaa s:0 i:0xa9 f:0x14 I ] op:0x20 arg1:0x1 arg2:0x18 s ] IMM d = 0x18 V ] a:0x44 b:0xb7 c:0 d:0x18 s:0 i:0xaa f:0x14 I ] op:0x10 arg1:0x12 arg2:0x1 j ] JMP LG dj ] ... TAKENV ] a:0x44 b:0xb7 c:0 d:0x18 s:0 i:0x19 f:0x14 I ] op:0x20 arg1:0x40 arg2:0xd4 s ] IMM b = 0xd4 V ] a:0x44 b:0xd4 c:0 d:0x18 s:0 i:0x1a f:0x14 I ] op:0x20 arg1:0x20 arg2:0xa s ] IMM c = 0xa V ] a:0x44 b:0xd4 c:0xa d:0x18 s:0 i:0x1b f:0x14 I ] op:0x20 arg1:0x2 arg2:0x1 s ] IMM a = 0x1 V ] a:0x1 b:0xd4 c:0xa d:0x18 s:0 i:0x1c f:0x14 I ] op:0x2 arg1:0x2 arg2:0x1 s ] SYS 0x2 ds ] ... write
rax+0x300是a1首地址,那么可以读出目标字符串
1 2 3 4 pwndbg > x /21 bx $rax+0 xb7 + 0 x300 -20 0x7ffe834dd363 : 0 x43 0 xed 0 xf2 0 x06 0 x74 0 x8f 0 xb8 0 x430x7ffe834dd36b : 0 xd0 0 x49 0 xd5 0 x94 0 x09 0 x9d 0 x9b 0 xf00x7ffe834dd373 : 0 xa6 0 x6c 0 xe7 0 x62 0 x5b
找到目标字符串,然后根据上述的vmcode能够找到对应的输入字符串,最后做一个减法即可。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 from pwn import *"/challenge/babyrev-level-20-0" )0x43 -0xa5 , 0xed -0xce , 0xf2 -0x67 , 0x06 -0xab , 0x74 -0x98 , 0x8f -0x46 , 0xb8 -0x63 , 0x43 -0xe1 , 0xd0 -0x48 ,0x49 -0x37 , 0xd5 -0x3e , 0x94 -0x7f , 0x09 -0xc1 , 0x9d -0xfa , 0x9b -0x53 , 0xf0 -0x5f , 0xa6 -0x99 , 0x6c -0x31 , 0xe7 -0x38 , 0x62 -0x8f , 0x5b - 0x89 ]b'' for i in range (len (al)):'B' , (al[i]) % 256 )while (z):print (z)
level20.1 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 220 221 222 223 224 225 226 227 228 229 230 231 232 233 234 235 236 237 238 239 240 241 242 243 244 245 246 247 248 249 250 251 252 253 254 255 256 257 258 259 260 261 262 263 264 265 266 267 268 269 270 271 272 273 274 275 276 277 278 279 280 281 282 283 284 285 286 287 288 289 290 291 292 293 294 295 296 297 298 299 300 301 302 303 304 305 306 307 308 309 310 311 312 313 314 315 316 317 318 319 320 321 322 323 324 325 326 327 328 329 330 331 332 333 334 335 336 337 338 339 340 341 342 343 344 345 346 347 348 349 350 351 352 353 354 355 356 357 358 359 360 361 362 363 364 365 366 367 368 369 370 371 372 373 374 375 376 377 378 379 380 381 382 383 384 385 386 387 388 389 390 391 392 393 394 395 396 397 398 a :0 b:0 c:0 d:0 s:0 i:1 f:0 0x140c6 # 40 : IMM b(1 ) = c6a :0 b:c6 c:0 d:0 s:0 i:2 f:0 0x80801 # 08 : stka :0 b:c6 c:0 d:0 s:0 i:c7 f:0 0x140c2 a :0 b:c2 c:0 d:0 s:0 i:c8 f:0 0x104005 # 40 : IMM c(0 x10) = 05 a :0 b:c2 c:5 d:0 s:0 i:c9 f:0 0x404001 # 40 : IMM a(0 x40) = 0 a :1 b:c2 c:5 d:0 s:0 i:ca f:0 0x48002 # 80 :SYSa :1 b:c2 c:5 d:5 s:0 i:cb f:0 0x840 a :1 b:c2 c:5 d:5 s:1 i:cc f:0 0x801 a :1 b:c2 c:5 d:5 s:2 i:cd f:0 0x810 a :1 b:c2 c:5 d:5 s:3 i:ce f:0 0x14030 a :1 b:30 c:5 d:5 s:3 i:cf f:0 0x104022 a :1 b:30 c:22 d:5 s:3 i:d0 f:0 0x404000 a :0 b:30 c:22 d:5 s:3 i:d1 f:0 0x18002 a :0 b:30 c:22 d:15 s:3 i:d2 f:0 0x100800 a :0 b:30 c:5 d:15 s:2 i:d3 f:0 0x10800 a :0 b:c2 c:5 d:15 s:1 i:d4 f:0 0x400800 a :1 b:c2 c:5 d:15 s:0 i:d5 f:0 0x84002 a :1 b:c2 c:5 d:15 s:0 i:3 f:0 0x840 a :1 b:c2 c:5 d:15 s:1 i:4 f:0 0x801 a :1 b:c2 c:5 d:15 s:2 i:5 f:0 0x810 a :1 b:c2 c:5 d:15 s:3 i:6 f:0 0x404030 a :30 b:c2 c:5 d:15 s:3 i:7 f:0 0x1040fe a :30 b:c2 c:fe d:15 s:3 i:8 f:0 0x10140 # 01 : LDM b = *aa :30 b:9 e c:fe d:15 s:3 i:9 f:0 0x11010 # 10 : ADD b ca :30 b:9 c c:fe d:15 s:3 i:a f:0 0x400201 # 02 : STM a = *b a1[0 x30] = user1 + 0 xfe a :30 b:9 c c:fe d:15 s:3 i:b f:0 0x404031 a :31 b:9 c c:fe d:15 s:3 i:c f:0 0x10409b a :31 b:9 c c:9 b d:15 s:3 i:d f:0 0x10140 a :31 b:1 f c:9 b d:15 s:3 i:e f:0 0x11010 a :31 b:ba c:9 b d:15 s:3 i:f f:0 0x400201 # 02 : STM a = *b a1[0 x31] = user2 + 0 x9ba :31 b:ba c:9 b d:15 s:3 i:10 f:0 0x404032 a :32 b:ba c:9 b d:15 s:3 i:11 f:0 0x10403c a :32 b:ba c:3 c d:15 s:3 i:12 f:0 0x10140 a :32 b:8 b c:3 c d:15 s:3 i:13 f:0 0x11010 a :32 b:c7 c:3 c d:15 s:3 i:14 f:0 0x400201 a :32 b:c7 c:3 c d:15 s:3 i:15 f:0 0x404033 a :33 b:c7 c:3 c d:15 s:3 i:16 f:0 0x1040cc a :33 b:c7 c:cc d:15 s:3 i:17 f:0 0x10140 a :33 b:5 b c:cc d:15 s:3 i:18 f:0 0x11010 a :33 b:27 c:cc d:15 s:3 i:19 f:0 0x400201 a :33 b:27 c:cc d:15 s:3 i:1 a f:0 0x404034 a :34 b:27 c:cc d:15 s:3 i:1 b f:0 0x1040e3 a :34 b:27 c:e3 d:15 s:3 i:1 c f:0 0x10140 a :34 b:dc c:e3 d:15 s:3 i:1 d f:0 0x11010 a :34 b:bf c:e3 d:15 s:3 i:1 e f:0 0x400201 a :34 b:bf c:e3 d:15 s:3 i:1 f f:0 0x404035 a :35 b:bf c:e3 d:15 s:3 i:20 f:0 0x1040b0 a :35 b:bf c:b0 d:15 s:3 i:21 f:0 0x10140 a :35 b:49 c:b0 d:15 s:3 i:22 f:0 0x11010 a :35 b:f9 c:b0 d:15 s:3 i:23 f:0 0x400201 a :35 b:f9 c:b0 d:15 s:3 i:24 f:0 0x404036 a :36 b:f9 c:b0 d:15 s:3 i:25 f:0 0x10401e a :36 b:f9 c:1 e d:15 s:3 i:26 f:0 0x10140 a :36 b:55 c:1 e d:15 s:3 i:27 f:0 0x11010 a :36 b:73 c:1 e d:15 s:3 i:28 f:0 0x400201 a :36 b:73 c:1 e d:15 s:3 i:29 f:0 0x404037 a :37 b:73 c:1 e d:15 s:3 i:2 a f:0 0x1040e6 a :37 b:73 c:e6 d:15 s:3 i:2 b f:0 0x10140 a :37 b:62 c:e6 d:15 s:3 i:2 c f:0 0x11010 a :37 b:48 c:e6 d:15 s:3 i:2 d f:0 0x400201 a :37 b:48 c:e6 d:15 s:3 i:2 e f:0 0x404038 a :38 b:48 c:e6 d:15 s:3 i:2 f f:0 0x104088 a :38 b:48 c:88 d:15 s:3 i:30 f:0 0x10140 a :38 b:88 c:88 d:15 s:3 i:31 f:0 0x11010 a :38 b:10 c:88 d:15 s:3 i:32 f:0 0x400201 a :38 b:10 c:88 d:15 s:3 i:33 f:0 0x404039 a :39 b:10 c:88 d:15 s:3 i:34 f:0 0x104012 a :39 b:10 c:12 d:15 s:3 i:35 f:0 0x10140 a :39 b:12 c:12 d:15 s:3 i:36 f:0 0x11010 a :39 b:24 c:12 d:15 s:3 i:37 f:0 0x400201 a :39 b:24 c:12 d:15 s:3 i:38 f:0 0x40403a a :3 a b:24 c:12 d:15 s:3 i:39 f:0 0x1040a1 a :3 a b:24 c:a1 d:15 s:3 i:3 a f:0 0x10140 a :3 a b:97 c:a1 d:15 s:3 i:3 b f:0 0x11010 a :3 a b:38 c:a1 d:15 s:3 i:3 c f:0 0x400201 a :3 a b:38 c:a1 d:15 s:3 i:3 d f:0 0x40403b a :3 b b:38 c:a1 d:15 s:3 i:3 e f:0 0x1040d3 a :3 b b:38 c:d3 d:15 s:3 i:3 f f:0 0x10140 a :3 b b:15 c:d3 d:15 s:3 i:40 f:0 0x11010 a :3 b b:e8 c:d3 d:15 s:3 i:41 f:0 0x400201 a :3 b b:e8 c:d3 d:15 s:3 i:42 f:0 0x40403c a :3 c b:e8 c:d3 d:15 s:3 i:43 f:0 0x1040c3 a :3 c b:e8 c:c3 d:15 s:3 i:44 f:0 0x10140 a :3 c b:48 c:c3 d:15 s:3 i:45 f:0 0x11010 a :3 c b:b c:c3 d:15 s:3 i:46 f:0 0x400201 a :3 c b:b c:c3 d:15 s:3 i:47 f:0 0x40403d a :3 d b:b c:c3 d:15 s:3 i:48 f:0 0x104002 a :3 d b:b c:2 d:15 s:3 i:49 f:0 0x10140 a :3 d b:a3 c:2 d:15 s:3 i:4 a f:0 0x11010 a :3 d b:a5 c:2 d:15 s:3 i:4 b f:0 0x400201 a :3 d b:a5 c:2 d:15 s:3 i:4 c f:0 0x40403e a :3 e b:a5 c:2 d:15 s:3 i:4 d f:0 0x1040b2 a :3 e b:a5 c:b2 d:15 s:3 i:4 e f:0 0x10140 a :3 e b:48 c:b2 d:15 s:3 i:4 f f:0 0x11010 a :3 e b:fa c:b2 d:15 s:3 i:50 f:0 0x400201 a :3 e b:fa c:b2 d:15 s:3 i:51 f:0 0x40403f a :3 f b:fa c:b2 d:15 s:3 i:52 f:0 0x1040df a :3 f b:fa c:df d:15 s:3 i:53 f:0 0x10140 a :3 f b:91 c:df d:15 s:3 i:54 f:0 0x11010 a :3 f b:70 c:df d:15 s:3 i:55 f:0 0x400201 a :3 f b:70 c:df d:15 s:3 i:56 f:0 0x404040 a :40 b:70 c:df d:15 s:3 i:57 f:0 0x104095 a :40 b:70 c:95 d:15 s:3 i:58 f:0 0x10140 a :40 b:d c:95 d:15 s:3 i:59 f:0 0x11010 a :40 b:a2 c:95 d:15 s:3 i:5 a f:0 0x400201 a :40 b:a2 c:95 d:15 s:3 i:5 b f:0 0x404041 a :41 b:a2 c:95 d:15 s:3 i:5 c f:0 0x1040f6 a :41 b:a2 c:f6 d:15 s:3 i:5 d f:0 0x10140 a :41 b:3 b c:f6 d:15 s:3 i:5 e f:0 0x11010 a :41 b:31 c:f6 d:15 s:3 i:5 f f:0 0x400201 a :41 b:31 c:f6 d:15 s:3 i:60 f:0 0x404042 a :42 b:31 c:f6 d:15 s:3 i:61 f:0 0x104098 a :42 b:31 c:98 d:15 s:3 i:62 f:0 0x10140 a :42 b:af c:98 d:15 s:3 i:63 f:0 0x11010 a :42 b:47 c:98 d:15 s:3 i:64 f:0 0x400201 a :42 b:47 c:98 d:15 s:3 i:65 f:0 0x404043 a :43 b:47 c:98 d:15 s:3 i:66 f:0 0x104057 a :43 b:47 c:57 d:15 s:3 i:67 f:0 0x10140 a :43 b:d3 c:57 d:15 s:3 i:68 f:0 0x11010 a :43 b:2 a c:57 d:15 s:3 i:69 f:0 0x400201 a :43 b:2 a c:57 d:15 s:3 i:6 a f:0 0x404044 a :44 b:2 a c:57 d:15 s:3 i:6 b f:0 0x104066 a :44 b:2 a c:66 d:15 s:3 i:6 c f:0 0x10140 a :44 b:d2 c:66 d:15 s:3 i:6 d f:0 0x11010 a :44 b:38 c:66 d:15 s:3 i:6 e f:0 0x400201 a :44 b:38 c:66 d:15 s:3 i:6 f f:0 0x404045 a :45 b:38 c:66 d:15 s:3 i:70 f:0 0x10400c a :45 b:38 c:c d:15 s:3 i:71 f:0 0x10140 a :45 b:0 c:c d:15 s:3 i:72 f:0 0x11010 a :45 b:c c:c d:15 s:3 i:73 f:0 0x400201 a :45 b:c c:c d:15 s:3 i:74 f:0 0x404046 a :46 b:c c:c d:15 s:3 i:75 f:0 0x104077 a :46 b:c c:77 d:15 s:3 i:76 f:0 0x10140 a :46 b:0 c:77 d:15 s:3 i:77 f:0 0x11010 a :46 b:77 c:77 d:15 s:3 i:78 f:0 0x400201 a :46 b:77 c:77 d:15 s:3 i:79 f:0 0x404047 a :47 b:77 c:77 d:15 s:3 i:7 a f:0 0x1040e5 a :47 b:77 c:e5 d:15 s:3 i:7 b f:0 0x10140 a :47 b:0 c:e5 d:15 s:3 i:7 c f:0 0x11010 a :47 b:e5 c:e5 d:15 s:3 i:7 d f:0 0x400201 a :47 b:e5 c:e5 d:15 s:3 i:7 e f:0 0x404048 a :48 b:e5 c:e5 d:15 s:3 i:7 f f:0 0x10406d a :48 b:e5 c:6 d d:15 s:3 i:80 f:0 0x10140 a :48 b:0 c:6 d d:15 s:3 i:81 f:0 0x11010 a :48 b:6 d c:6 d d:15 s:3 i:82 f:0 0x400201 a :48 b:6 d c:6 d d:15 s:3 i:83 f:0 0x404049 a :49 b:6 d c:6 d d:15 s:3 i:84 f:0 0x104042 a :49 b:6 d c:42 d:15 s:3 i:85 f:0 0x10140 a :49 b:0 c:42 d:15 s:3 i:86 f:0 0x11010 a :49 b:42 c:42 d:15 s:3 i:87 f:0 0x400201 a :49 b:42 c:42 d:15 s:3 i:88 f:0 0x40404a a :4 a b:42 c:42 d:15 s:3 i:89 f:0 0x1040bf a :4 a b:42 c:bf d:15 s:3 i:8 a f:0 0x10140 a :4 a b:0 c:bf d:15 s:3 i:8 b f:0 0x11010 a :4 a b:bf c:bf d:15 s:3 i:8 c f:0 0x400201 a :4 a b:bf c:bf d:15 s:3 i:8 d f:0 0x40404b a :4 b b:bf c:bf d:15 s:3 i:8 e f:0 0x10401c a :4 b b:bf c:1 c d:15 s:3 i:8 f f:0 0x10140 a :4 b b:0 c:1 c d:15 s:3 i:90 f:0 0x11010 a :4 b b:1 c c:1 c d:15 s:3 i:91 f:0 0x400201 # 最后一个, STM *a = b, a1[0 x4b] = user28 + 1 ca :4 b b:1 c c:1 c d:15 s:3 i:92 f:0 0x100800 a :4 b b:1 c c:5 d:15 s:2 i:93 f:0 0x10800 a :4 b b:c2 c:5 d:15 s:1 i:94 f:0 0x400800 a :1 b:c2 c:5 d:15 s:0 i:95 f:0 0x840d5 a :1 b:c2 c:5 d:15 s:0 i:d6 f:0 0x404030 a :30 b:c2 c:5 d:15 s:0 i:d7 f:0 0x14080 a :30 b:80 c:5 d:15 s:0 i:d8 f:0 0x10401c a :30 b:80 c:1 c d:15 s:0 i:d9 f:0 0x24002 a :30 b:80 c:1 c d:2 s:0 i:da f:0 0x21008 a :30 b:80 c:1 c d:dc s:0 i:db f:0 0x802 a :30 b:80 c:1 c d:dc s:1 i:dc f:0 0x84095 a :30 b:80 c:1 c d:dc s:1 i:96 f:0 0x401010 a :4 c b:80 c:1 c d:dc s:1 i:97 f:0 0x11010 a :4 c b:9 c c:1 c d:dc s:1 i:98 f:0 0x240ff a :4 c b:9 c c:1 c d:ff s:1 i:99 f:0 0x401002 a :4 b b:9 c c:1 c d:ff s:1 i:9 a f:0 0x11002 a :4 b b:9 b c:1 c d:ff s:1 i:9 b f:0 0x840 a :4 b b:9 b c:1 c d:ff s:2 i:9 c f:0 0x801 a :4 b b:9 b c:1 c d:ff s:3 i:9 d f:0 0x400140 # 01 : LDM a = *aa :1 c b:9 b c:1 c d:ff s:3 i:9 e f:0 0x10101 # 01 : LDM b = *ba :1 c b:63 c:1 c d:ff s:3 i:9 f f:0 0x400401 # 04 : CMP a b === cmp a1[0 x4b] a1[0 x9b]a :1 c b:63 c:1 c d:ff s:3 i:a0 f:c0x10800 a :1 c b:9 b c:1 c d:ff s:2 i:a1 f:c0x400800 a :4 b b:9 b c:1 c d:ff s:1 i:a2 f:c0x240a9 a :4 b b:9 b c:1 c d:a9 s:1 i:a3 f:c0x82002 a :4 b b:9 b c:1 c d:a9 s:1 i:aa f:c0x20810 a :4 b b:9 b c:1 c d:1 c s:1 i:ab f:c0x80800 a :4 b b:9 b c:1 c d:1 c s:0 i:dd f:c0x104000 a :4 b b:9 b c:0 d:1 c s:0 i:de f:c0x20410 a :4 b b:9 b c:0 d:1 c s:0 i:df f:a0x240b1 a :4 b b:9 b c:0 d:b1 s:0 i:e0 f:a0x102002 a :4 b b:9 b c:0 d:b1 s:0 i:e1 f:a0x240ab a :4 b b:9 b c:0 d:ab s:0 i:e2 f:a0x62002 a :4 b b:9 b c:0 d:ab s:0 i:ac f:a0x140b8 a :4 b b:b8 c:0 d:ab s:0 i:ad f:a0x10400a a :4 b b:b8 c:a d:ab s:0 i:ae f:a0x404001 a :1 b:b8 c:a d:ab s:0 i:af f:a0x48002 a :1 b:b8 c:a d:a s:0 i:b0 f:a0x404001 a :1 b:b8 c:a d:a s:0 i:b1 f:a0x88000
起始位置没有变,还是$rax + 0x300,加上我们的偏移就是$rax + 0x300 + 0x9b - 27,最后拿到目标字符串
1 2 3 4 5 pwndbg > x /28 bx $rax + 0 x300 +0 x9b -27 0x7ffd7698ca20 : 0 x38 0 x62 0 x4d 0 x42 0 x6e 0 xdf 0 x72 0 xff0x7ffd7698ca28 : 0 x09 0 x8e 0 x2b 0 x6f 0 x1e 0 xc8 0 x03 0 xe20x7ffd7698ca30 : 0 x53 0 x3b 0 x07 0 xfd 0 x79 0 x6e 0 x01 0 x570x7ffd7698ca38 : 0 xa8 0 x61 0 xa8 0 x63
最后得出exp,但是我感觉我手动的有点麻烦,后面数据多的话写个脚本处理吧。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 from pwn import *"/challenge/babyrev-level-20-1" )0x38 -0xfe , 0x62 -0x9b , 0x4d -0x3c , 0x42 -0xcc , 0x6e -0xe3 , 0xdf -0xb0 , 0x72 -0x1e , 0xff -0xe6 , 0x9 -0x88 , 0x8e -0x12 , 0x2b -0xa1 , 0x6f -0xd3 , 0x1e -0xc3 , 0xc8 -0x02 , 0x03 -0xb2 , 0xe2 -0xdf , 0x53 -0x95 , 0x3b -0xf6 , 0x07 -0x98 , 0xfd -0x57 , 0x79 -0x66 , 0x6e -0xc , 0x01 -0x77 , 0x57 -0xe5 , 0xa8 -0x6d , 0x61 -0x42 , 0xa8 -0xbf ,0x63 - 0x1c ]print (len (al))b'' for i in range (len (al)):'B' , (al[i]) % 256 )while (z):print (z)
level21.0 这题需要自己写yancode,可以参考20.0,然后调试它。可以发现yancode是以三个字节三个字节作为一个指令的。也就是一个opcode加两个参数。那么根据不同的opcode和参数做出不同的操作。
这里需要做的是:将/flag字符串写入内存中,然后调用open,也就是SYS open打开/flag。它会返回一个文件描述符,通常为0x3。然后再调用SYS read,将0x3读入到内存中,它会返回读入的字节数,就是flag的长度为0x39。最后使用SYS write把内存中的flag读出来。exp如下:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 from pwn import *"/challenge/babyrev-level-21-0" )b'' 0x403010 "big" )[1 :]0x402f40 "big" )[1 :]0x204010 "big" )[1 :] 0x403110 "big" )[1 :]0x406640 "big" )[1 :]0x204010 "big" )[1 :] 0x403210 "big" )[1 :]0x406c40 "big" )[1 :]0x204010 "big" )[1 :] 0x403310 "big" )[1 :]0x406140 "big" )[1 :]0x204010 "big" )[1 :] 0x403410 "big" )[1 :]0x406740 "big" )[1 :]0x204010 "big" )[1 :] 0x403010 "big" )[1 :]0x400040 "big" )[1 :]0x081008 "big" )[1 :]0x404040 "big" )[1 :]0x40ff08 "big" )[1 :]0x080801 "big" )[1 :]0x400110 "big" )[1 :]0x404040 "big" )[1 :]0x080820 "big" )[1 :] 0x084004 "big" )[1 :]print (payload)for i in range (100 ):print (p.readline())
level21.1 1 2 3 4 5 6 7 8 40 imm80 add02 stk04 stm01 ldm20 cmp10 jmp8 sys
1 2 3 4 5 6 7 64 a 8 b 32 c1 d16 s4 i 2 f
ida把对应的变量替换。因为每次指令对应的opcode以及变量对应的变量code都会变化。因此这里做一个替换。
不过替换之后还是有问题,通过gdb调试过程中发现,参数顺序换了。也就是arg1 和 arg2又恢复成正常顺序了,上面那题arg1 和 arg2是反着的。最后exp:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 from pwn import *"/challenge/babyrev-level-21-1" )b'' 0x404030 "big" )[1 :]0x40082f "big" )[1 :]0x044008 "big" )[1 :] 0x404031 "big" )[1 :]0x400866 "big" )[1 :]0x044008 "big" )[1 :] 0x404032 "big" )[1 :]0x40086c "big" )[1 :]0x044008 "big" )[1 :] 0x404033 "big" )[1 :]0x400861 "big" )[1 :]0x044008 "big" )[1 :] 0x404034 "big" )[1 :]0x400867 "big" )[1 :]0x044008 "big" )[1 :] 0x404030 "big" )[1 :]0x400800 "big" )[1 :]0x082040 "big" )[1 :]0x400840 "big" )[1 :]0x4020ff "big" )[1 :]0x080420 "big" )[1 :]0x404001 "big" )[1 :]0x400840 "big" )[1 :]0x081020 "big" )[1 :] 0x080108 "big" )[1 :]print (payload)for i in range (100 ):print (p.readline())
level22.0 因为opcode和var_code的总数不是很多,可以记录一下。
opcode
op
0x1
ADD
0x2
IMM
0x4
STK
0x8
JMP
0x10
LDM
0x20
SYS
0x40
STM
0x80
CMP
变量记录如下:
变量
Code
a
0x04
b
0x40
c
0x01
d
0x10
s
0x02
i
0x80
f
0x08
并且测试的时候发现,arg1在三字节的第一个位置,arg2在三字节中的第二个位置,opcode在最后。
关于SYS而言,Sleep是08,write是01,read_code是04,open是20,exit是40,read是80
针对SYS指令,第一个字节是syscode,第二个位置是变量code,第三个位置是opcode。
这种情况下,改exp就很快了。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 from pwn import *"/challenge/babyrev-level-22-0" )b'' 0x043002 "big" )[1 :]0x402f02 "big" )[1 :]0x044040 "big" )[1 :] 0x043102 "big" )[1 :]0x406602 "big" )[1 :]0x044040 "big" )[1 :] 0x043202 "big" )[1 :]0x406c02 "big" )[1 :]0x044040 "big" )[1 :] 0x043302 "big" )[1 :]0x406102 "big" )[1 :]0x044040 "big" )[1 :] 0x043402 "big" )[1 :]0x406702 "big" )[1 :]0x044040 "big" )[1 :] 0x043002 "big" )[1 :]0x400002 "big" )[1 :]0x200420 "big" )[1 :]0x404002 "big" )[1 :]0x01ff02 "big" )[1 :]0x800120 "big" )[1 :]0x040102 "big" )[1 :]0x404002 "big" )[1 :]0x010420 "big" )[1 :] 0x0400420 "big" )[1 :]print (payload)for i in range (200 ):print (p.readline())
level22.1 根据discord以及一些别人的wp,发现得查看Crash信息,才能知道。跑一下爆破脚本:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 import subprocessfrom pwn import *'/challenge/babyrev-level-22-0' ]bytearray ()with open ('res.txt' , 'w' ) as file:'' )0x01 , 0x02 , 0x04 , 0x08 , 0x10 , 0x20 , 0x40 , 0x80 ]for i in values:0x31 ) for j in values:print (data.hex ())try :input =data,stdout=subprocess.PIPE, stderr=subprocess.PIPE,timeout=2 )with open ('res.txt' ,'ab' ) as file:hex ().encode('ascii' ))1074 :])except subprocess.TimeoutExpired:print ("timeout" ,data.hex ())
对于22.0跑出来的结果如下(过滤出超时的部分):
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 timeout 310108 timeout 310208 timeout 310408 timeout 310808 timeout 311008 timeout 312008 timeout 314008 timeout 318008 timeout 310120 timeout 310220 timeout 310420 timeout 310820 timeout 311020 timeout 314020 timeout 318020
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 220 221 222 223 224 225 226 227 228 229 230 231 232 233 234 235 236 237 238 239 240 241 242 243 244 245 246 247 248 249 250 251 252 253 254 255 256 257 258 259 260 261 310101open
根据观察,可以发现:IMM,ADD,STK,LDM,STM和CMP不会出现Timeout。SYS和JMP会出现超时, 但是SYS open不会出现超时。
那么回推到level22.1:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 300101 timeout 300101 300201 timeout 300201 300401 timeout 300401 300801 timeout 300801 301001 timeout 301001 302001 timeout 302001 304001 timeout 304001 308001 timeout 308001 300120 timeout 300120 300220 timeout 300220 300420 timeout 300420 300820 timeout 300820 301020 timeout 301020 302020 timeout 302020 304020 308020 timeout 308020
能够确定,01是JMP指令,20是SYS指令。且xx4020是open syscall。
然后我们把arg1改成0x00后发现(timeout设置为1):
对level22.0来说,JMP,STK和SYS都会超时7个。
对于level22.1来说,01,80会超时7个,20会超时8个。
80是STK指令
把arg1改成0x10后发现:
对于level22.0来说,JMP和IMM都会超时8个,其余超时7个。
对于level22.1来说,01和02超时8个,其余超时7个。
02是IMM指令
把arg1改成0x20后发现:
对于level22.0来说,JMP超时8个,SYS超时7个(open不超时),其余不超时。
对于level22.1来说,01和02超时8个,其余超时7个。
把arg1改成0x40后发现:
对于level22.0来说,SYS都不超因为是exit,JMP,IMM全超时,其余超时7个。
对于level22.1来说,opcode20和opcode01超时。其余都不超时。
把arg1改成0x01后发现:
对于level22.1来说,SYS都不超时,JMP和IMM超时8个。其余超时7个,因此结合0x40参数来说,可以确定0x01是exit参数。随后可以使用imm + exit来确定i寄存器的位置。超时说明imm赋值了i寄存器,导致控制流改变,没有正确退出。得出i为08
总结一下:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 JMP : 01IMM : 02SYS : 20 | open:40 exit:01STK : 80STM : ?LDM : ?ADD : ?CMP : ?- ------------------------------------a : ?b : ?c : ?d : ?s : ?i : 08f : ?
到这儿以后,根据之前的shellcode发现,指令这块儿只拿到STM就够了。那么如何让STM在LDM,ADD,CMP中脱颖而出呢?依然是改变i寄存器的值,只要这个改变,那么控制流就会改变。而ADD和LDM都会改变i的值,因此会超时。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 import subprocessfrom pwn import *command = ['/challenge/babyrev-level-22 -1 ']data = bytearray()# with open('res.txt', 'w') as file: # file.write('') values = [0x04 , 0x08 , 0x10 , 0x40 ]for i in values:data .append(0x01 )data .append(0x30 )data .append(0x02 ) # IMM reg0x1 = 0x30data .append(0x08 ) # i寄存器data .append(0x01 ) # 0x1寄存器data .append(i ) # 依次改成04 08 10 40测试即可data .append(0x01 )data .append(0x01 )data .append(0x20 )data .hex())data ,stdout=subprocess.PIPE , stderr=subprocess.PIPE ,timeout=1)TimeoutExpired :"timeout" ,data .hex())data .clear()
结果为:
1 2 3 4 5 6 013002080104010120 timeout 013002080104010120 013002080108010120 013002080110010120 013002080140010120 timeout 013002080140010120
因此,可以判断出ADD指令和LDM指令在0x04和0x40中。而STM指令和CMP指令在0x08和0x10中。
进一步区STM和CMP指令需要借助JMP指令。因为CMP+JMP指令会导致跳转,从而超时。但是STM+JMP指令不会导致跳转。所以,CMP+JMP测试:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 import subprocessfrom pwn import *'/challenge/babyrev-level-22-1' ]bytearray ()0x08 , 0x10 ]0x01 , 0x02 , 0x04 , 0x08 , 0x10 , 0x20 , 0x40 , 0x80 ]for i in values:for j in values_2:0x01 )0x30 )0x02 ) 0x08 ) 0x08 ) 0x01 )0x01 )0x01 )0x01 )0x20 )print (data.hex ())try :input =data,stdout=subprocess.PIPE, stderr=subprocess.PIPE,timeout=1 )except subprocess.TimeoutExpired:print ("timeout" ,data.hex ())
这里对于JMP指令的参数是不知道的,因此也需要循环遍历。所以是双重循环。最后结果如下:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 hacker@reverse -engineering~level22-1 :~/Desktop $ python vm.py 013002080808010101010120 013002080808020101010120 013002080808040101010120 013002080808080101010120 013002080808100101010120 013002080808200101010120 013002080808400101010120 013002080808800101010120 013002080810010101010120 013002080810020101010120 013002080810040101010120 013002080810080101010120 013002080810100101010120 013002080810200101010120 013002080810400101010120 013002080810400101010120 013002080810800101010120
因此,确定到080810中10是CMP指令。则08是STM指令的opcode。最后总结一下:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 JMP : 01IMM : 02SYS : 20 | open:40 exit:01STK : 80STM : 08LDM : 04|40ADD : 04|40CMP : 10- ------------------------------------a : ?b : ?c : ?d : ?s : ?i : 08f : ?
接下来通过SYS sleep来确定reg_a,因为SYS sleep会休眠reg_a秒。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 import subprocessfrom pwn import *'/challenge/babyrev-level-22-1' ]bytearray ()0x02 , 0x4 , 0x08 , 0x10 ,0x20 , 0x80 ]0x01 , 0x02 , 0x04 , 0x10 , 0x20 , 0x40 , 0x80 ]for i in values:for j in values_2:0x10 )0x02 ) 0x1 ) 0x20 )0x01 )0x01 )0x20 )print (data.hex ())try :input =data,stdout=subprocess.PIPE, stderr=subprocess.PIPE,timeout=5 )except subprocess.TimeoutExpired:print ("timeout" ,data.hex ())
结果为:timeout 101002020120010120。那么可以知道0x10为reg_a,且sleep的code为0x02。再次汇总:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 JMP: 01 IMM: 02 SYS: 20 | open:40 exit:01 sleep :02 STK: 80 STM: 08 LDM: 04 |40 ADD: 04 |40 CMP: 10 a: 10 b: ?c: ?d: ?s: ?i: 08 f: ?
接下来可以确定write,因为可以将rax置为0x1这样就会输出在屏幕中了,因此我们可以遍历rcx,因为rcx控制的是输出字符数量,再遍历read | write | read_code。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 import subprocessfrom pwn import *command = ['/challenge/babyrev-level-22 -1 ']data = bytearray()# with open('res.txt', 'w') as file: # file.write('') values = [0x4 , 0x08 , 0x10 ,0x20 , 0x80 ]values_2 = [0x01 , 0x02 , 0x04 , 0x20 , 0x40 , 0x80 ]for i in values:in values_2:data .append(j )data .append(0x01 )data .append(0x02 ) # IMM c = 0x01data .append(0x10 )data .append(0x01 )data .append(0x02 ) # IMM a = 0x01data .append(i )data .append(0x01 ) # write | read_code | read_memdata .append(0x20 )data .append(0x01 )data .append(0x01 )data .append(0x20 )data .hex())data ,stdout=subprocess.PIPE , stderr=subprocess.PIPE ,timeout=1)TimeoutExpired :"timeout" ,data .hex())data .clear()
查看结果,可以找到长度不一致的输入。这个就是我们找到的write和rcx:
1 2 3 4 5 6 7 8 9 10 800102100102080120010120 1075 010102100102100120010120 1075 020102100102100120010120 1076 040102100102100120010120 1075 200102100102100120010120 1075
那么可以知道,write是0x10,rcx是0x02。然后read也很简单,写一个exp,并且使用interactive,如果这个interactive一直在等待输入,那么说明是read_memory或者read_code。exp:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 from pwn import *"/challenge/babyrev-level-22-1" )b'' 0x020102 "big" )[1 :]0x100002 "big" )[1 :]0x201020 "big" )[1 :]0x010120 "big" )[1 :]print (payload)
最终确定,read_mem和read_code是20和08之中的。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 JMP: 01 IMM: 02 SYS: 20 | open:04 | 40 exit:01 sleep :02 write:10 read:08 |20 STK: 80 STM: 08 LDM: 04 |40 ADD: 04 |40 CMP: 10 a: 10 b: 04 c: 02 d: 01 |04 |20 |80 s: 01 |04 |20 |80 i: 08 f: 01 |04 |20 |80
最后,即可使用Shellcode的爆破。依次去试出来。
这里发现了一个错误…因为一开始错误的认为Open是0x40导致后面的exp一直出不来。最后试了一下0x4出来了。因此如果open有问题,那么就也进行一个尝试即可。